350-901: Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Part 3
Question #: 121
Topic #: 1
There is a requirement to securely store unique usernames and passwords. Given a valid username, it is also required to validate that the password provided is correct.
Which action accomplishes this task?
A. Encrypt the username, hash the password, and store these values.
B. Hash the username, hash the password, and store these values.
C. Encrypt the username, encrypt the password, and store these values.
D. Hash the username, encrypt the password, and store these values.
Selected Answer: A
Question #: 122
Topic #: 1
While developing an application following the 12-factor app methodology, which approach should be used in the application for logging?
A. Write a log to a file in the application directory.
B. Write a log to a file in /var/log.
C. Write the logs buffered to stdout.
D. Write the logs unbuffered to stdout.
Selected Answer: D
Question #: 123
Topic #: 1
An application has initiated an OAuth authorization code grant flow to get access to an API resource on behalf of an end user.
Which two parameters are specified in the HTTP request coming back to the application as the end user grants access? (Choose two.)
A. access token and a refresh token with respective expiration times to access the API resource
B. access token and expiration time to access the API resource
C. redirect URI a panel that shows the list of permissions to grant
D. code that can be exchanged for an access token
E. state can be used for correlation and security checks
Selected Answer: DE
Question #: 124
Topic #: 1
A web application is susceptible to cross-site scripting.
Which two methods allow this issue to be mitigated? (Choose two.)
A. Use only drop downs.
B. Limit user input to acceptable characters.
C. Encrypt user input on the client side.
D. Use AES encryption to secure the script.
E. Remove all HTML/XML tags from user input.
Selected Answer: BE
Question #: 125
Topic #: 1
Why is end-to-end encryption deployed when exposing sensitive data through APIs?
A. Data transfers are untraceable from source to destination.
B. Data cannot be read or modified other than by the true source and destination.
C. Server-side encryption enables the destination to control data protection.
D. Traffic is encrypted and decrypted at every hop in the network path.
Selected Answer: B
Question #: 126
Topic #: 1
A developer deploys a SQLite database in a Docker container. Single-use secret keys are generated each time a user accesses the database. The keys expire after 24 hours.
Where should the keys be stored?
A. Outside of the Docker container in the source code of applications that connect to the SQLite database.
B. In a separate file inside the Docker container that runs the SQLite database.
C. In an encrypted database table within the SQLite database.
D. In a separate storage volume within the Docker container.
Selected Answer: D
Question #: 127
Topic #: 1
While working with the Webex API, on an application that uses end-to-end encryption, a webhook has been received. What must be considered to read the message?
A. Webhook information cannot be used to read the message because of end-to-end encryption. The API key is needed to decrypt the message.
B. Webhook returns the full unencrypted message. Only the body is needed to query the API.
C. Webhook returns a hashed version of the message that must be unhashed with the API key.
D. Webhook returns message identification. To query, the API is needed for that message to get the decrypted information.
Selected Answer: D
Question #: 128
Topic #: 1
When end-to-end encryption is implemented, which area is most vulnerable to exploitation?
A. cryptographic key exchange
B. endpoint security
C. cryptographic key generation
D. security of data in transit
Selected Answer: B
Question #: 129
Topic #: 1
How do end-to-end encryption principles apply to APIs?
A. The owners of the service are prevented from accessing data that is being transferred.
B. Sensitive information is protected against backdoor attacks.
C. The API data is protected against man-in-the-middle attacks.
D. Both endpoints that are using the API resources are hardened against hacking.
Selected Answer: C
Question #: 130
Topic #: 1
What is a data privacy concern when designing data storage?
A. Data must be kept for as long as necessary.
B. Storage must be designed to enable data maximization.
C. Data must be retained in secure data storage after use.
D. Storage must be designed to enforce encryption in transit.
Selected Answer: A
Question #: 131
Topic #: 1
A web application is being developed to provide online sales to a retailer. The customers will need to use their username and passwords to login into their profile and complete their order. For this reason, the application must store user passwords.
Which approach ensures that an attacker will need to crack the passwords one at a time?
A. Store the passwords by using asymmetric encryption.
B. Apply the salting technique.
C. Store the passwords by using symmetric encryption.
D. Apply the peppering technique.
Selected Answer: B
Question #: 132
Topic #: 1
DRAG DROP –
An engineer is developing a web-based application that will be used as a central repository for the HR department. The application needs to authenticate user access and encrypt communication. Drag and drop the steps from the left into the order on the right to install an application-specific SSL certificate.
Select and Place:

Suggestion Answer:

Question #: 133
Topic #: 1
Refer to the exhibit. What is the missing step in deploying a Docker container to IOx?
A. Build the package.yaml file.
B. Pull/push the image to the Docker registry.
C. Build the package.cert file to sign the app.
D. Log in to Device Manager.
Selected Answer: A
Question #: 134
Topic #: 1
Refer to the exhibit. The command docker build –tag=friendlyhello . is run to build a docker image from the given Dockerfile, reguirements.txt, and app.py. Then the command docker run -p 4000:80 friendlyhello is executed to run the application.
Which URL is entered in the web browser to see the content served by the application?
A. http://127.0.0.1:80
B. http://4000:80
C. http://localhost:4000
D. http://localhost:80
Selected Answer: C
Question #: 135
Topic #: 1
What is an effective logging strategy according to the 12-factor app tenets?
A. Tag and save logs in a local document database that has querying capabilities.
B. Back up log files in a high-availability remote cluster on the public cloud.
C. Timestamp and save logs in a local time-series database that has querying capabilities.
D. Capture logs by the execution environment and route to a centralized destination.
Selected Answer: D
Question #: 136
Topic #: 1
Refer to the exhibit. Pipenv is used to manage dependencies. The test runs successfully on a local environment.
What is the reason for the error when running the test on a CI/CD pipeline?
A. All the unit tests in testsum.py failed.
B. Pytest did not detect any functions that start with ‘test_’.
C. The pipfile in the local environment was not pushed to the remote repository.
D. Nose2 was not used as the test runner.
Selected Answer: C
Question #: 137
Topic #: 1
What are two benefits of using a centralized logging service? (Choose two.)
A. reduces the time required to query log data across multiple hosts
B. reduces the loss of logs after a single disk failure
C. improves application performance by reducing CPU usage
D. improves application performance by reducing memory usage
E. provides compression and layout of log data
Selected Answer: AE
Question #: 138
Topic #: 1
A team of developers created their own CA and started signing certificates for all of their IoT devices.
Which action will make the browser accept these certificates?
A. Install a TLS instead of SSL certificate on the IoT devices.
B. Set the private keys 1024-bit RSA.
C. Preload the developer CA on the trusted CA list of the browser.
D. Enable HTTPS or port 443 on the browser.
Selected Answer: C
Question #: 139
Topic #: 1
DRAG DROP –
An engineer must access multiple bots that are running in an internal infrastructure. A different HTTPS URL is required for each bot. The infrastructure has just one public IP address and a Linux server with Apache installed. Drag and drop the actions from the left into the order of steps on the right to enable access to the bots inside. Not all options are used.
Select and Place:

Suggestion Answer:

Question #: 140
Topic #: 1
What are two benefits of using distributed log collectors? (Choose two.)
A. supports multiple transport protocols such as TCP/UDP
B. improves performance and reduces resource consumption
C. provides flexibility due to a wide range of plugins and accepted log formats
D. enables extension of logs with fields and export to backend systems
E. buffers and resends data when the network is unavailable
Selected Answer: BE
Question #: 141
Topic #: 1
Refer to the exhibit. A company has extended networking from the data center to the cloud through Transit VPC.
Which two statements describe the benefits of this approach? (Choose two.)
A. Dynamic routing combined with multi-AZ deployment creates a robust network infrastructure.
B. VPC virtual gateways provide highly available connections to virtual networks.
C. Dedicated VPC simplifies load balancing by combining internal and external web services.
D. VPC virtual gateways provide more secure connections to virtual networks.
E. Dedicated VPC simplifies routing by not combining this service with other shared services.
Selected Answer: AE
Question #: 142
Topic #: 1
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?
A. Embed them directly in the code.
B. Store them in a hidden file.
C. Store them inside the source tree of the application.
D. Change them periodically.
Selected Answer: D
Question #: 143
Topic #: 1
Which two principles are included in the codebase tenet of the 12-factor app methodology? (Choose two.)
A. An application is always tracked in a version control system.
B. There are multiple codebases per application.
C. The codebase is the same across all deploys.
D. There can be a many-to-one correlation between codebase and application.
E. It is only possible to have one application deployment per codebase.
Selected Answer: AC
Question #: 144
Topic #: 1
What is submitted when an SSL certificate is requested?
A. PEM
B. CRT
C. DER
D. CSR
Selected Answer: D
Question #: 145
Topic #: 1
Which two actions must be taken when an observable microservice application is developed? (Choose two.)
A. Know the state of a single instance of a single service.
B. Place ג€try/exceptג€ statement in code.
C. Place log statements in the code.
D. Use distributed tracing techniques.
E. Deploy microservice to multiple datacenters.
Selected Answer: CD
Question #: 146
Topic #: 1
Which two countermeasures help reduce the risk of playback attacks? (Choose two.)
A. Store data in a NoSQL database.
B. Implement message authentication (HMAC).
C. Enable end-to-end encryption.
D. Remove stack traces from errors.
E. Use short-lived access tokens.
Selected Answer: BE
Question #: 147
Topic #: 1
Which type of file is created from issued intermediate, root, and primary certificates for SSL installation on a server?
A. DER
B. CSR
C. PEM
D. CRT
Selected Answer: C
Question #: 148
Topic #: 1
DRAG DROP –
Refer to the exhibit. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the curl exhibit to complete the cURL request to FirePower Device Manager API to create objects. Not all code snippets are used.
Select and Place:

Suggestion Answer:

Question #: 149
Topic #: 1
Which two statements describe advantages of static code analysis over unit tests? (Choose two.)
A. It checks for potential tainted data where input is not checked.
B. It enforces proper coding standards and style.
C. It performs a quick analysis of whether tests will pass or fail when run.
D. It checks for race conditions in threaded applications.
E. It estimates the performance of the code when run.
Selected Answer: AB
Question #: 150
Topic #: 1
Refer to the exhibit. Which additional line results in the output of Test 1 upon execution of the docker run –rm devnet 1 command in a Dockerfile with this content?
A. CMD [ג€/bin/echoג€, ג€Test1ג€] B. RUN [ג€/bin/echoג€, ג€Test1ג€] C. ENTRYPOINT [ג€/bin/echoג€, ג€Test1ג€] D. CMD [ג€/bin/echo Test1ג€]
Selected Answer: C
Question #: 151
Topic #: 1
Which two techniques protect against injection attacks? (Choose two.)
A. input validation
B. trim whitespace
C. limit text areas to 255 characters
D. string escaping of user free text and data entry
E. only use dropdown, checkbox, and radio button fields
Selected Answer: AD
Question #: 152
Topic #: 1
Refer to the exhibit. A kubeconfig file to manage access to clusters is provided.
How many clusters are defined and which of them are accessed using username/password authentication versus certificate?
A. two clusters; scratch
B. three clusters; scratch
C. three clusters; development
D. two clusters; development
Selected Answer: A
Question #: 153
Topic #: 1
Which two strategies are used to protect personally identifiable information? (Choose two.)
A. Encrypt data in transit.
B. Encrypt hash values of data.
C. Encrypt data at rest.
D. Only hash usernames and passwords for efficient lookup.
E. Only encrypt usernames and passwords for efficient lookup.
Selected Answer: AC
Question #: 154
Topic #: 1
The response from a server includes the header ETag: W/`7eb8b94419e371767916ef13e0d6e63d`. Which statement is true?
A. The ETag has a Strong validator directive.
B. The ETag has a Weak validator directive, which is an optional directive.
C. The ETag has a Weak validator directive, which is a mandatory directive.
D. The ETag has a Strong validator directive, which it is incorrectly formatted.
Selected Answer: B
Question #: 155
Topic #: 1
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
A. 202
B. 401
C. 429
D. 503
Selected Answer: C
Question #: 156
Topic #: 1
Refer to the exhibit. A Docker swarm cluster is configured to load balance services across data centers in three different geographical regions: west, central, and east. The cluster has three manager nodes and three worker nodes. A new service named cisco_devnet is being deployed. The service has these design requirements:
✑ All containers must be hosted only on nodes in the central region.
✑ The service must run only on nodes that are ineligible for the manager role.
Which approach fulfills the requirements?
A. Use placement constraints to control nodes to which the service can be assigned.
B. Create the service manually in the central region and set replicas to 0.
C. Enable the control flag in the containers of the west and east regions to prevent the service from starting.
D. Create a second swarm cluster that is hosted only in the central region.
Selected Answer: A
Question #: 157
Topic #: 1
An engineer is developing a Docker container for an application in Python. For security reasons the application needs to be accessible on port 5001 only. Which line should be added to the dockerfile in order to accomplish this?
A. ADD PORT 5001
B. ENTRYPOINT 5001
C. EXPOSE 5001
D. PORT SRC 5001
Selected Answer: C
Question #: 158
Topic #: 1
Refer to the exhibit. The cisco_devnet Docker swarm service runs across five replicas. The development team tags and imports a new image named devnet/ test:1.1 and requests that the image be upgraded on each container. There must be no service outages during the upgrade process. Which two design approaches must be used? (Choose two.)
A. Enable parallel upgrades by using the docker service update command.
B. Ensure that the service is hosted behind a VIP with no session persistence.
C. Ensure that the service replicas are set to a minimum of 5.
D. Update the restart policy of the containers to restart upon failure.
E. Implement rolling upgrades by using the docker service update command.
Selected Answer: BE
Question #: 159
Topic #: 1
Refer to the exhibit. An attempt to execute a CI/CD pipeline results in the error shown. What is the cause of the error?
A. The unit tests failed to complete.
B. The VCS repository is unavailable.
C. The remote library repository is unavailable.
D. The built artifacts failed to publish to the target server.
Selected Answer: B
Question #: 160
Topic #: 1
Refer to the exhibit. Which action should be performed to avoid an SQL injection attack?
A. Validate the input on the platform variable.
B. Develop a denial of service response plan.
C. Encrypt the password that is used to connect to the database.
D. Compile the Python file instead of allowing live interpretation.
Selected Answer: A
Question #: 161
Topic #: 1
Which scenario is an example of the pseudonymization of sensitive data that meets GDPR requirements?
A. implementing X-Forwarded-For at the frontend of a web app to enable the source IP addresses of headers to change
B. separating the sensitive data into its own dedicated, secured data store and using tokens in its place.
C. encrypting sensitive data at rest by using native cloud services and data in transit by using SSL/TLS transport.
D. leveraging an application load balancer at the frontend of a web app for SSL/TLS decryption to inspect data in transit.
Selected Answer: B
Question #: 162
Topic #: 1
A developer must deploy a containerized application for network device inventory management. The developer sets up a Kubernetes cluster on two separate hypervisors. The SLA is not currently meeting a specified maximum value for network latency/jitter. CPU/memory and disk I/O are functioning properly. Which two design approaches resolve the issue? (Choose two.)
A. Enable IPv6 within the cluster.
B. Upgrade the server NIC card.
C. Deploy the cluster to a bare metal server.
D. Replace the HDD drives with SSD drives.
E. Collocate services in the same pod.
Selected Answer: BC
Question #: 163
Topic #: 1
DRAG DROP –
Drag and drop the code from the bottom onto the box where the code is missing on the Ansible task to enable a VLAN on a Meraki MX device. Not all options are used.
Select and Place:
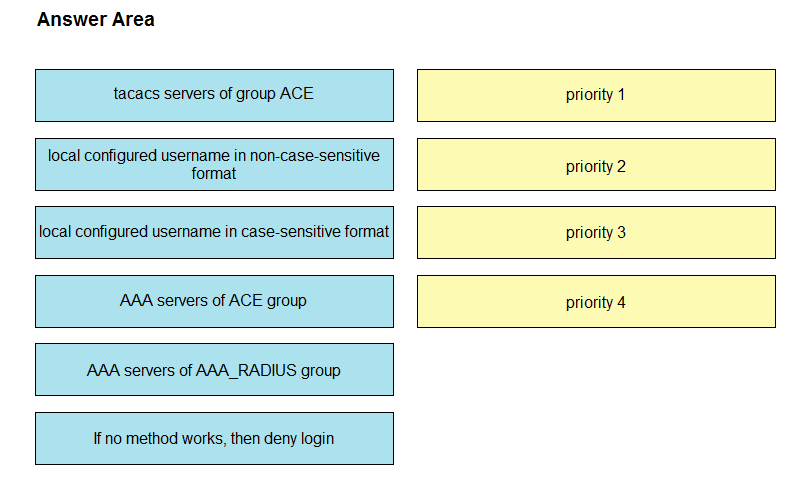
Suggestion Answer:
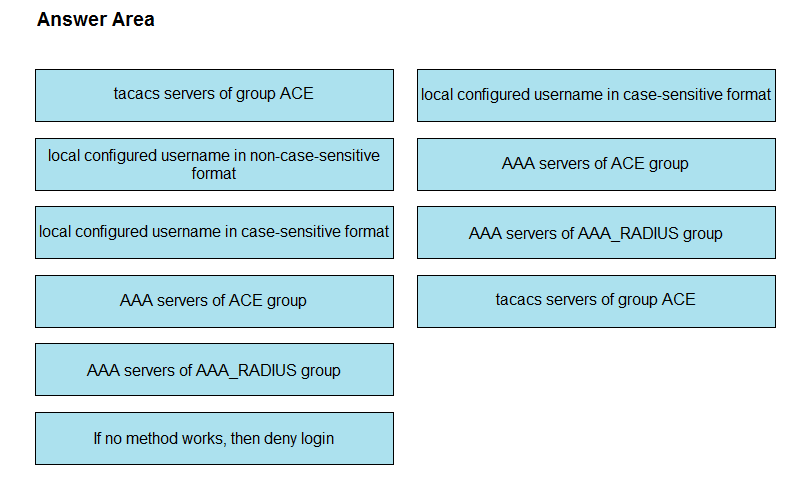
Question #: 164
Topic #: 1
DRAG DROP –
Drag and drop the code from the bottom onto the box where the code is missing in the snippet to complete this Ansible playbook. Not all options are used.
Select and Place:

Suggestion Answer:

Question #: 165
Topic #: 1
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates the NTP server peer?
A. state: absent
B. state: False
C. config: absent
D. config: False
Selected Answer: A
Question #: 166
Topic #: 1
A developer needs to configure an environment to orchestrate and configure.
Which two tools should be used for each task? (Choose two.)
A. Jenkins for orchestration
B. Terraform for orchestration
C. Bamboo for configuration
D. Kubernetes for orchestration
E. Ansible for configuration
Selected Answer: BE
Question #: 167
Topic #: 1
Refer to the exhibit. An engineer is configuring Ansible to run playbooks against Cisco IOS XE Software.
What should be configured in ansible.cfg as the connection type?
A. network_cli
B. ssh
C. shell
D. command
Selected Answer: A
Question #: 168
Topic #: 1
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module removes the NTP server peer?
A. state: absent
B. state: False
C. config: absent
D. config: False
Selected Answer: A
Question #: 169
Topic #: 1
DRAG DROP –
Drag and drop the code from the bottom of the code snippet to the blanks in the code to construct a Puppet manifest that configures a VRF instance on a Cisco
IOS XR device. Not all options are used.
Select and Place:

Suggestion Answer:

Question #: 170
Topic #: 1
Which tool is used to deploy an IOx application to a group of IOx devices at one time?
A. ioxclient
B. IOx local manager
C. Fog Network Director
D. Kubernetes
Selected Answer: A
Question #: 171
Topic #: 1
Which two files are needed to create a Cisco IOx application to host on a Cisco device that is running a Cisco IOS XE version older than 16.12? (Choose two.)
A. package_setup.py
B. package_config.ini
C. application.cfg
D. iox.cfg
E. package.yaml
Selected Answer: BE
Question #: 172
Topic #: 1
Which command is used to enable application hosting on a Cisco IOS XE device?
A. iox
B. application-hosting
C. iox-service
D. app-hosting
Selected Answer: D
Question #: 173
Topic #: 1
DRAG DROP –
Drag and drop the steps from the left into the order on the right to configure and install a container on a Cisco Catalyst 9000 Series Switch.
Select and Place:

Suggestion Answer:

Question #: 174
Topic #: 1
Refer to the exhibit. Which word is missing from this Ansible playbook shown, to allow the Cisco IOS XE commands for router configuration to be pushed after the playbook is executed?
A. input
B. lines
C. commands
D. config
Selected Answer: B
Question #: 175
Topic #: 1
Refer to the exhibit. The Ansible playbook is using the netconf_module to configure an interface using a YANG model. As part of this workflow, which YANG models augment the interface?
A. ietf-interfaces and ietf-ip
B. iana-if-type and ietf-interfaces
C. ietf-ip and openconfig-interface
D. ietf-ip and iana-if-type
Selected Answer: D
Question #: 176
Topic #: 1
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
A. state: present
B. state: True
C. config: present
D. config: True
Selected Answer: A
Question #: 177
Topic #: 1
Refer to the exhibit. The YAML represented is using the ios_vrf module.
As part of the Ansible playbook workflow, what is the result when this task is run?
A. VRFs not defined in the host_vars file are removed from the device.
B. VRFs not defined in the host_vars file are added to the device, and any other VRFs on the device remain.
C. VRFs defined in the host_vars file are removed from the device.
D. VRFs are added to the device from the host_vars file, and any other VRFs on the device are removed.
Selected Answer: D
Question #: 178
Topic #: 1
Refer to the exhibit. As part of the Ansible playbook workflow, several new interfaces are being configured using the netconf_config module. The task references the interface variables that are unique per device.
In which directory is the YAML file with these variables found?
A. host_vars directory
B. home directory
C. group_vars directory
D. current working directory
Selected Answer: A
Question #: 179
Topic #: 1
A developer needs to configure an environment to orchestrate and configure.
Which two tools should be used for each task? (Choose two.)
A. Puppet for orchestration
B. Terraform for orchestration
C. Terraform for configuration
D. Ansible for orchestration
E. Ansible for configuration
Selected Answer: BE
Question #: 180
Topic #: 1
Applications sometimes store configuration as constants in the code, which is a violation of the strict separation of configuration from code.
Where should application configuration be stored?
A. environment variables
B. YAML files
C. Python libraries
D. Dockerfiles
E. INI files
Selected Answer: A

