350-701: Implementing and Operating Cisco Security Core Technologies Part 3
Question #: 121
Topic #: 1
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?
A. authoring
B. consumption
C. sharing
D. analysis
Selected Answer: B
Question #: 122
Topic #: 1
An administrator is configuring a DHCP server to better secure their environment. They need to be able to rate-limit the traffic and ensure that legitimate requests are not dropped. How would this be accomplished?
A. Set a trusted interface for the DHCP server.
B. Set the DHCP snooping bit to 1.
C. Enable ARP inspection for the required VLAN.
D. Add entries in the DHCP snooping database.
Selected Answer: A
Question #: 123
Topic #: 1
What is a prerequisite when integrating a Cisco ISE server and an AD domain?
A. Configure a common administrator account.
B. Place the Cisco ISE server and the AD server in the same subnet.
C. Synchronize the clocks of the Cisco ISE server and the AD server.
D. Configure a common DNS server.
Selected Answer: C
Question #: 124
Topic #: 1
When configuring ISAKMP for IKEv1 Phase 1 on a Cisco IOS router, an administrator needs to input the command crypto isakmp key cisco address 0.0.0.0.
The administrator is not sure what the IP address in this command is used for. What would be the effect of changing the IP address from 0.0.0.0 to 1.2.3.4?
A. The key server that is managing the keys for the connection will be at 1.2.3.4.
B. The address that will be used as the crypto validation authority.
C. All IP addresses other than 1.2.3.4 will be allowed.
D. The remote connection will only be allowed from 1.2.3.4.
Selected Answer: A
Question #: 125
Topic #: 1
A network administrator is configuring SNMPv3 on a new router. The users have already been created, however an additional configuration is needed to facilitate access to the SNMP views. What must the administrator do to accomplish this?
A. define the encryption algorithm to be used by SNMPv3
B. set the password to be used for SNMPv3 authentication
C. map SNMPv3 users to SNMP views
D. specify the UDP port used by SNMP
Selected Answer: B
Question #: 126
Topic #: 1
DRAG DROP –
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
Select and Place:

Suggestion Answer:

Question #: 127
Topic #: 1
Refer to the exhibit. When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine certificates. Which configuration item must be modified to allow this?
A. Method
B. SAML Server
C. AAA Server Group
D. Group Policy
Selected Answer: A
Question #: 128
Topic #: 1
An administrator is trying to determine which applications are being used in the network but does not want the network devices to send metadata to Cisco
Firepower. Which feature should be used to accomplish this?
A. Network Discovery
B. Access Control
C. Packet Tracer
D. NetFlow
Selected Answer: A
Question #: 129
Topic #: 1
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command ntp authentication-key 1 md5 Cisc392481137. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however is unable to do so. Which command is required to enable the client to accept the server’s authentication key?
A. ntp server 1.1.1.2 key 1
B. ntp peer 1.1.1.2 key 1
C. ntp server 1.1.1.1 key 1
D. ntp peer 1.1.1.1 key 1
Selected Answer: C
Question #: 130
Topic #: 1
Due to a traffic storm on the network, two interfaces were error-disabled, and both interfaces sent SNMP traps. Which two actions must be taken to ensure that interfaces are put back into service? (Choose two.)
A. Enable the snmp-server enable traps command and wait 300 seconds.
B. Use EEM to have the ports return to service automatically in less than 300 seconds
C. Ensure that interfaces are configured with the error-disable detection and recovery feature.
D. Have Cisco Prime Infrastructure issue an SNMP set command to re-enable the ports after the preconfigured interval.
E. Enter the shutdown and no shutdown commands on the interfaces.
Selected Answer: CE
Question #: 131
Topic #: 1
Refer to the exhibit. An administrator is adding a new Cisco FTD device to their network and wants to manage it with Cisco FMC. The Cisco FTD uses a registration key of Cisc392481137 and is not behind a NAT device. Which command is needed to enable this on the Cisco FTD?
A. configure manager add 16
B. configure manager add DONTRESOLVE FTD123
C. configure manager add
D. configure manager add DONTRESOLVE
Selected Answer: A
Question #: 132
Topic #: 1
A network administrator needs to find out what assets currently exist on the network. Third-party systems need to be able to feed host data into Cisco Firepower.
What must be configured to accomplish this?
A. a Network Analysis policy to receive NetFlow data from the host
B. a File Analysis policy to send file data into Cisco Firepower
C. a Network Discovery policy to receive data from the host
D. a Threat Intelligence policy to download the data from the host
Selected Answer: A
Question #: 133
Topic #: 1
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior of users?
A. file access from a different user
B. user login suspicious behavior
C. privilege escalation
D. interesting file access
Selected Answer: A
Question #: 134
Topic #: 1
Which attribute has the ability to change during the RADIUS CoA?
A. authorization
B. NTP
C. accessibility
D. membership
Selected Answer: A
Question #: 135
Topic #: 1
An administrator configures new authorization policies within Cisco ISE and has difficulty profiling the devices. Attributes for the new Cisco IP phones that are profiled based on the RADIUS authentication are seen; however, the attributes for CDP or DHCP are not. What should the administrator do to address this issue?
A. Configure a service template within the switch to standardize the port configurations so that the correct information is sent to Cisco ISE.
B. Configure the ip dhcp snooping trust command on the DHCP interfaces to get the information to Cisco ISE.
C. Configure the authentication port-control auto feature within Cisco ISE to identify the devices that are trying to connect.
D. Configure the device sensor feature within the switch to send the appropriate protocol information.
Selected Answer: D
Question #: 136
Topic #: 1
An organization deploys multiple Cisco FTD appliances and wants to manage them using one centralized solution. The organization does not have a local VM but does have existing Cisco ASA that must migrate over to Cisco FTDs. Which solution meets the needs of the organization?
A. Cisco FMC
B. CDO
C. CSM
D. Cisco FDM
Selected Answer: B
Question #: 137
Topic #: 1
What is a benefit of using telemetry over SNMP to configure new routers for monitoring purposes?
A. Telemetry uses push and pull, which makes it more secure than SNMP.
B. Telemetry uses push and pull, which makes it more scalable than SNMP.
C. Telemetry uses a push method, which makes it faster than SNMP.
D. Telemetry uses a pull method, which makes it more reliable than SNMP.
Selected Answer: C
Question #: 138
Topic #: 1
Refer to the exhibit. A network engineer is testing NTP authentication and realizes that any device synchronizes time with this router and that NTP authentication is not enforced. What is the cause of this issue?
A. The hashing algorithm that was used was MD5, which is unsupported.
B. The key was configured in plain text.
C. NTP authentication is not enabled.
D. The router was not rebooted after the NTP configuration updated.
Selected Answer: B
Question #: 139
Topic #: 1
An engineer has been tasked with configuring a Cisco FTD to analyze protocol fields and detect anomalies in the traffic from industrial systems. What must be done to meet these requirements?
A. Enable traffic analysis in the Cisco FTD.
B. Implement pre-filter policies for the CIP preprocessor.
C. Configure intrusion rules for the DNP3 preprocessor.
D. Modify the access control policy to trust the industrial traffic.
Selected Answer: C
Question #: 140
Topic #: 1
An organization uses Cisco FMC to centrally manage multiple Cisco FTD devices. The default management port conflicts with other communications on the network and must be changed. What must be done to ensure that all devices can communicate together?
A. Change the management port on Cisco FMC so that it pushes the change to all managed Cisco FTD devices.
B. Set the sftunnel port to 8305.
C. Manually change the management port on Cisco FMC and all managed Cisco FTD devices.
D. Set the sftunnel to go through the Cisco FTD.
Selected Answer: C
Question #: 141
Topic #: 1
An administrator is establishing a new site-to-site VPN connection on a Cisco IOS router. The organization needs to ensure that the ISAKMP key on the hub is used only for terminating traffic from the IP address of 172.19.20.24. Which command on the hub will allow the administrator to accomplish this?
A. crypto isakmp identity address 172.19.20.24
B. crypto ca identity 172.19.20.24
C. crypto enrollment peer address 172.19.20.24
D. crypto isakmp key Cisco0123456789 172.19.20.24
Selected Answer: B
Question #: 142
Topic #: 1
A Cisco FTD engineer is creating a newIKEv2 policy called s2s00123456789 for their organization to allow additional protocols to terminate network devices with.
They currently only have one policy established and need the new policy to be a backup in case some devices cannot support the stronger algorithms listed in the primary policy. What should be done in order to support this?
A. Change the encryption to AES* to support all AES algorithms in the primary policy.
B. Make the priority for the primary policy 10 and the new policy 1.
C. Change the integrity algorithms to SHA* to support all SHA algorithms in the primary policy.
D. Make the priority for the new policy 5 and the primary policy 1.
Selected Answer: D
Question #: 143
Topic #: 1
What is a functional difference between a Cisco ASA and Cisco IOS router with Zone-Based Policy Firewall?
A. The Cisco ASA can be configured for high availability, whereas the Cisco IOS router with Zone-Based Policy Firewall cannot.
B. The Cisco IOS router with Zone-Based Policy Firewall can be configured for high availability, whereas the Cisco ASA cannot.
C. The Cisco ASA denies all traffic by default, whereas the Cisco IOS router with Zone-Based Policy Firewall starts out by allowing all traffic, even on untrusted interfaces.
D. The Cisco IOS router with Zone-Based Policy Firewall denies all traffic by default, whereas Cisco ASA starts out by allowing traffic until rules are added.
Selected Answer: D
Question #: 144
Topic #: 1
An engineer is configuring their router to send NetfFow data to Stealthwatch which has an IP address of 1.1.1.1 using the flow record Stealthwatch406143794 command. Which additional command is required to complete the flow record?
A. cache timeout active 60
B. destination 1.1.1.1
C. match ipv4 ttl
D. transport udp 2055
Selected Answer: C
Question #: 145
Topic #: 1
An engineer is adding a Cisco DUO solution to the current TACACS+ deployment using Cisco ISE. The engineer wants to authenticate users using their account when they log into network devices. Which action accomplishes this task?
A. Configure Cisco DUO with the external Active Directory connector and tie it to the policy set within Cisco ISE.
B. Install and configure the Cisco DUO Authentication Proxy and configure the identity source sequence within Cisco ISE.
C. Modify the current policy with the condition MFA: SourceSequence:DUO=true in the authorization conditions within Cisco ISE.
D. Create an identity policy within Cisco ISE to send all authentication requests to Cisco DUO.
Selected Answer: B
Question #: 146
Topic #: 1
What is the function of the crypto isakmp key cisc406143794 address 0.0.0.0 0.0.0.0 command when establishing an IPsec VPN tunnel?
A. It prevents all IP addresses from connecting to the VPN server.
B. It configures the pre-shared authentication key.
C. It configures the local address for the VPN server.
D. It defines what data is going to be encrypted via the VPN.
Selected Answer: C
Question #: 147
Topic #: 1
An administrator is adding a new switch onto the network and has configured AAA for network access control. When testing the configuration, the RADIUS authenticates to Cisco ISE but is being rejected. Why is the ip radius source-interface command needed for this configuration?
A. Only requests that originate from a configured NAS IP are accepted by a RADIUS server.
B. The RADIUS authentication key is transmitted only from the defined RADIUS source interface.
C. RADIUS requests are generated only by a router if a RADIUS source interface is defined.
D. Encrypted RADIUS authentication requires the RADIUS source interface be defined.
Selected Answer: A
Question #: 148
Topic #: 1
Which statement about the configuration of Cisco ASA NetFlow v9 Secure Event Logging is true?
A. To view bandwidth usage for NetFlow records, the QoS feature must be enabled.
B. A sysopt command can be used to enable NSEL on a specific interface.
C. NSEL can be used without a collector configured.
D. A flow-export event type must be defined under a policy.
Selected Answer: A
Question #: 149
Topic #: 1
Which feature requires a network discovery policy on the Cisco Firepower NGIPS?
A. security intelligence
B. impact flags
C. health monitoring
D. URL filtering
Selected Answer: B
Question #: 150
Topic #: 1
What is a characteristic of traffic storm control behavior?
A. Traffic storm control drops all broadcast and multicast traffic if the combined traffic exceeds the level within the interval.
B. Traffic storm control cannot determine if the packet is unicast or broadcast.
C. Traffic storm control monitors incoming traffic levels over a 10-second traffic storm control interval.
D. Traffic storm control uses the Individual/Group bit in the packet source address to determine if the packet is unicast or broadcast.
Selected Answer: B
Question #: 151
Topic #: 1
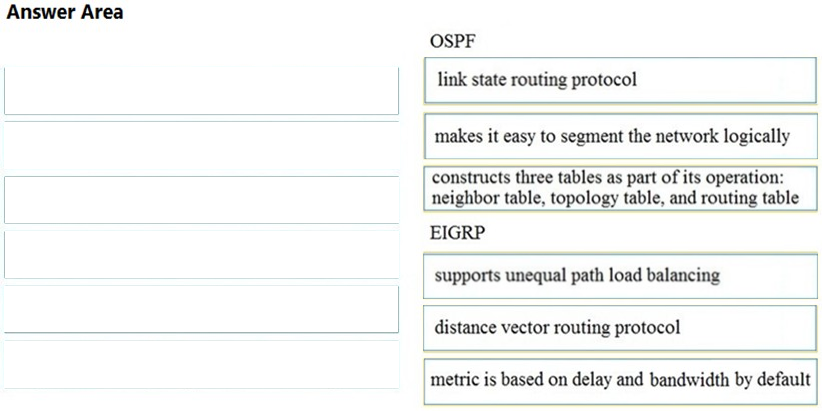
DRAG DROP –
Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right.
Select and Place:
Suggestion Answer:

Question #: 152
Topic #: 1
Refer to the exhibit. Which statement about the authentication protocol used in the configuration is true?
A. The authentication request contains only a password
B. The authentication request contains only a username
C. The authentication and authorization requests are grouped in a single packet.
D. There are separate authentication and authorization request packets.
Selected Answer: B
Question #: 153
Topic #: 1
Which deployment model is the most secure when considering risks to cloud adoption?
A. public cloud
B. hybrid cloud
C. community cloud
D. private cloud
Selected Answer: D
Question #: 154
Topic #: 1
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
A. It allows the administrator to quarantine malicious files so that the application can function, just not maliciously.
B. It discovers and controls cloud apps that are connected to a company’s corporate environment.
C. It deletes any application that does not belong in the network.
D. It sends the application information to an administrator to act on.
Selected Answer: D
Question #: 155
Topic #: 1
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries?
A. DNS tunneling
B. DNSCrypt
C. DNS security
D. DNSSEC
Selected Answer: C
Question #: 156
Topic #: 1
Which technology reduces data loss by identifying sensitive information stored in public computing environments?
A. Cisco SDA
B. Cisco Firepower
C. Cisco HyperFlex
D. Cisco Cloudlock
Selected Answer: D
Question #: 157
Topic #: 1
In which cloud services model is the tenant responsible for virtual machine OS patching?
A. IaaS
B. UCaaS
C. PaaS
D. SaaS
Selected Answer: A
Question #: 158
Topic #: 1
What is the function of Cisco Cloudlock for data security?
A. data loss prevention
B. controls malicious cloud apps
C. detects anomalies
D. user and entity behavior analytics
Selected Answer: A
Question #: 159
Topic #: 1
Which feature is supported when deploying Cisco ASAv within AWS public cloud?
A. multiple context mode
B. user deployment of Layer 3 networks
C. IPv6
D. clustering
Selected Answer: B
Question #: 160
Topic #: 1
Which cloud service model offers an environment for cloud consumers to develop and deploy applications without needing to manage or maintain the underlying cloud infrastructure?
A. PaaS
B. XaaS
C. IaaS
D. SaaS
Selected Answer: A
Question #: 161
Topic #: 1
Which risk is created when using an Internet browser to access cloud-based service?
A. misconfiguration of Infra, which allows unauthorized access
B. intermittent connection to the cloud connectors
C. vulnerabilities within protocol
D. insecure implementation of API
Selected Answer: C
Question #: 162
Topic #: 1
What is the Cisco API-based broker that helps reduce compromises, application risks, and data breaches in an environment that is not on-premise?
A. Cisco AppDynamics
B. Cisco Cloudlock
C. Cisco Umbrella
D. Cisco AMP
Selected Answer: B
Question #: 163
Topic #: 1
Which two aspects of the cloud PaaS model are managed by the customer but not the provider? (Choose two.)
A. middleware
B. applications
C. virtualization
D. operating systems
E. data
Selected Answer: C
Question #: 164
Topic #: 1
Which public cloud provider supports the Cisco Next Generation Firewall Virtual?
A. Google Cloud Platform
B. Red Hat Enterprise Virtualization
C. Amazon Web Services
D. VMware ESXi
Selected Answer: C
Question #: 165
Topic #: 1
What is an attribute of the DevSecOps process?
A. security scanning and theoretical vulnerabilities
B. development security
C. isolated security team
D. mandated security controls and check lists
Selected Answer: B
Question #: 166
Topic #: 1
On which part of the IT environment does DevSecOps focus?
A. application development
B. wireless network
C. data center
D. perimeter network
Selected Answer: C
Question #: 167
Topic #: 1
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two.)
A. Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
B. Cisco FTDv with one management interface and two traffic interfaces configured
C. Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
D. Cisco FTDv with two management interfaces and one traffic interface configured
E. Cisco FTDv configured in routed mode and IPv6 configured
Selected Answer: D
Question #: 168
Topic #: 1
DRAG DROP –
Drag and drop the steps from the left into the correct order on the right to enable Cisco AppDynamics to monitor an EC2 instance in AWS.
Select and Place:

Suggestion Answer:

Question #: 169
Topic #: 1
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
A. Enable IP Layer enforcement.
B. Activate the Cisco AMP license.
C. Activate SSL decryption.
D. Enable Intelligent Proxy.
Selected Answer: D
Question #: 170
Topic #: 1
A company is experiencing exfiltration of credit card numbers that are not being stored on-premise. The company needs to be able to protect sensitive data throughout the full environment. Which tool should be used to accomplish this goal?
A. Cisco ISE
B. Web Security Appliance
C. Security Manager
D. Cloudlock
Selected Answer: D
Question #: 171
Topic #: 1
What are the two types of managed Intercloud Fabric deployment models? (Choose two.)
A. Service Provider managed
B. User managed
C. Public managed
D. Hybrid managed
E. Enterprise managed
Selected Answer: AE
Question #: 172
Topic #: 1
An engineer needs a cloud solution that will monitor traffic, create incidents based on events, and integrate with other cloud solutions via an API. Which solution should be used to accomplish this goal?
A. CASB
B. Cisco Cloudlock
C. Adaptive MFA
D. SIEM
Selected Answer: B
Question #: 173
Topic #: 1
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally manage cloud policies across these platforms. Which software should be used to accomplish this goal?
A. Cisco Defense Orchestrator
B. Cisco Configuration Professional
C. Cisco Secureworks
D. Cisco DNA Center
Selected Answer: A
Question #: 174
Topic #: 1
Which factor must be considered when choosing the on-premise solution over the cloud-based one?
A. With an on-premise solution, the provider is responsible for the installation and maintenance of the product, whereas with a cloud-based solution, the customer is responsible for it.
B. With a cloud-based solution, the provider is responsible for the installation, but the customer is responsible for the maintenance of the product.
C. With an on-premise solution, the provider is responsible for the installation, but the customer is responsible for the maintenance of the product.
D. With an on-premise solution, the customer is responsible for the installation and maintenance of the product, whereas with a cloud-based solution, the provider is responsible for it.
Selected Answer: D
Question #: 175
Topic #: 1
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users, data, and applications. There is a requirement to use the Cisco cloud-native CASB and cloud cybersecurity platform. What should be used to meet these requirements?
A. Cisco NGFW
B. Cisco Cloudlock
C. Cisco Cloud Email Security
D. Cisco Umbrella
Selected Answer: D
Question #: 176
Topic #: 1
In an IaaS cloud services model, which security function is the provider responsible for managing?
A. firewalling virtual machines
B. Internet proxy
C. hypervisor OS hardening
D. CASB
Selected Answer: C
Question #: 177
Topic #: 1
An organization wants to secure users, data, and applications in the cloud. The solution must be API-based on operate as a cloud-native CASB. Which solution must be used for this implementation?
A. Cisco Cloud Email Security
B. Cisco Cloudlock
C. Cisco Umbrella
D. Cisco Firepower Nest-Generation Firewall
Selected Answer: B
Question #: 178
Topic #: 1
DRAG DROP –
Drag and drop the cloud security assessment components from the left onto the definitions on the right.
Select and Place:

Suggestion Answer:

Question #: 179
Topic #: 1
An organization wants to secure data in a cloud environment. Its security model requires that all users be authenticated and authorized. Security configuration and posture must be continuously validated before access is granted or maintained to applications and data. There is also a need to allow certain application traffic and deny all other traffic by default. Which technology must be used to implement these requirements?
A. virtual routing and forwarding
B. access control policy
C. virtual LAN
D. microsegmentation
Selected Answer: B
Question #: 180
Topic #: 1
Which cloud model is a collaborative effort where infrastructure is shared and jointly accessed by several organizations from a specific group?
A. community
B. private
C. public
D. hybrid
Selected Answer: A

