200-901: DevNet Associate (DEVASC) Part 6
Question #: 301
Topic #: 1
What is the purpose of running tests before writing code in test-driven development?
A. to find unexpected failures in the tests
B. to demonstrate that the tests fail for expected reasons
C. to ensure that the tests pass
D. to provide proof of the work carried out
Selected Answer: B
Question #: 302
Topic #: 1
Which port does HTTPS use by default?
A. 433
B. 443
C. 803
D. 883
Selected Answer: B
Question #: 303
Topic #: 1
Which HTTP method is used by webhooks and notifies a listener about an event change?
A. PUT
B. POST
C. PATCH
D. GET
Selected Answer: B
Question #: 304
Topic #: 1
A developer completed the creation of a script using Git. Before delivering it to the customer, the developer wants to be sure about all untracked files, without losing any information. Which command gathers this information?
A. git clean –n
B. git rm –f
C. git clean –r
D. git rm *
Selected Answer: A
Question #: 305
Topic #: 1
A company deploys an application via containers in its local data center. As soon as the application goes into production, it starts to crash at specific hours of the day. After investigation, it is concluded that the crashes are due to too many users accessing the application simultaneously. The spikes must be addressed and allow for future growth without discarding the investment already made. Which deployment model must be used?
A. hybrid cloud
B. edge
C. private cloud
D. public cloud
Selected Answer: A
Question #: 306
Topic #: 1
Which TCP port is used to connect to a network device by using Telnet?
A. 23
B. 69
C. 400
D. 830
Selected Answer: A
Question #: 307
Topic #: 1
Refer to the exhibit. Which action does the script perform?
A. It queries user credentials from Cisco IOS XE devices.
B. It retrieves device identification from Cisco DNA Center.
C. It exports SSID information from Meraki dashboard.
D. It collects group information from ACI.
Selected Answer: D
Question #: 308
Topic #: 1
What is the purpose of grouping devices in a VLAN?
A. Devices communicate as if they are connected on the same wire.
B. Multicast network traffic is limited to the VLAN connected devices.
C. Unicast messages are limited to the clients connected on the same VLAN.
D. Network traffic is load balanced between the devices connected to the VLAN.
Selected Answer: A
Question #: 309
Topic #: 1
Refer to the exhibit. The YAML shown contains an object “param0” that is equal to “Workflow1”, a second object “param1” that contains an object called “list” which contains an array of two objects, “name” (equal to “VLAN_ID”) and “value” (equal to a text value “198”), and finally a third object “param2” that is equal to “0”. What is the equivalent message in JSON data format?
A.
B.
C.
D.
Selected Answer: D
Question #: 310
Topic #: 1
An engineer prepares a set of Python scripts to interact with network devices. To avoid network performance issues, the engineer wants to run them in a test environment. Which resource must be used to monitor the live execution of code in an always-available environment?
A. packet tracer
B. learning labs
C. sandbox
D. code exchange
Selected Answer: C
Question #: 311
Topic #: 1
When a Cisco IOS XE networking device is configured by using RESTCONF, what is the default data encoding method?
A. application/yaml-data+json
B. application/yang-data+json
C. application/xml-data+json
D. application/json-data+xml
Selected Answer: B
Question #: 312
Topic #: 1
Refer to the exhibit. A developer is part of a team that is working on an open-source project in which source code is hosted in a public GitHub repository. While the application was built, security concerns were addressed by encrypting the credentials on the server. After a few months, the developer realized that a hacker managed to gain access to the account. The exhibit contains part of the source code for the login process. Why was the attacker able to access the developer’s account?
A. The encoded credentials were available in the source code.
B. The application was not encrypting the communication with the server.
C. The credentials were encrypted in the source code.
D. An SSL certificate was used instead of the TLS protocol to authenticate.
Selected Answer: A
Question #: 313
Topic #: 1
Which technology is responsible for matching a name to an IP address of an application running on a host?
A. firewall
B. proxy
C. load balancer
D. DNS
Selected Answer: D
Question #: 314
Topic #: 1
Which network constraint causes the performance of the application to decrease as the number of users accessing the application increases?
A. latency
B. loss
C. bandwidth
D. jitter
Selected Answer: C
Question #: 315
Topic #: 1
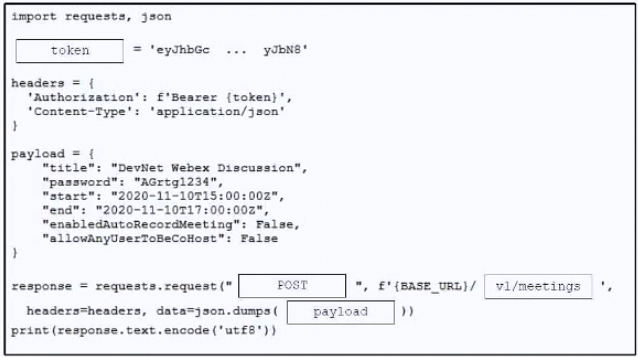
DRAG DROP
–
Refer to the exhibit. A bespoke meeting booking system must be integrated with Cisco Webex so that meetings are created automatically. Drag and drop the code from the bottom onto the box where the code is missing to create a sample meeting. Not all options are used.
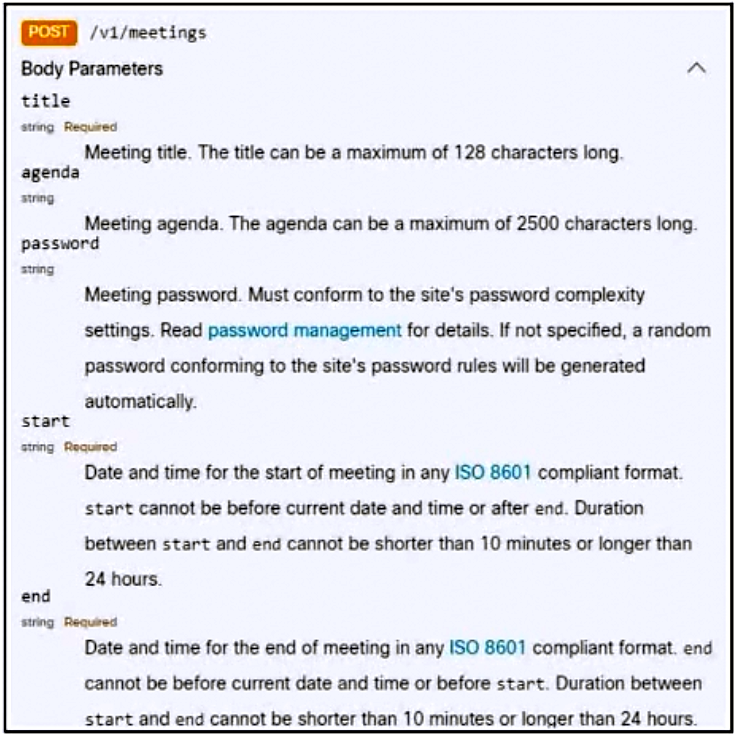
Suggestion Answer:
Question #: 316
Topic #: 1
What is a characteristic of Waterfall compared to Agile software development method?
A. Waterfall focuses on continuous improvement, and Agile focuses on the design phase.
B. Waterfall separates the project development lifecycle into sprints, and Agile does not use cycles.
C. Waterfall specifies requirements before development begins, and Agile responds flexibly to changes in requirements.
D. Waterfall uses reviews with step by step approach, and Agile uses a serially phased approach.
Selected Answer: C
Question #: 317
Topic #: 1
Users cannot access a webserver and after the traffic is captured, the capture tool snows an ICMP packet that reports “time exceeded in-transit”. What is the cause of this webserver access issue?
A. The large distance between the server and the users means that the packets require too much time to reach the destination.
B. A router along the path is misrouting the packets in a wrong direction.
C. A router along the path has the wrong time.
D. The server is overloaded and the connection was not able to be processed in time.
Selected Answer: B
Question #: 318
Topic #: 1
Refer to the exhibit. An engineer is comparing two files by using the unified diff format. Which cade snippet belongs to the new.py file?
A.
B.
C.
D.
Selected Answer: A
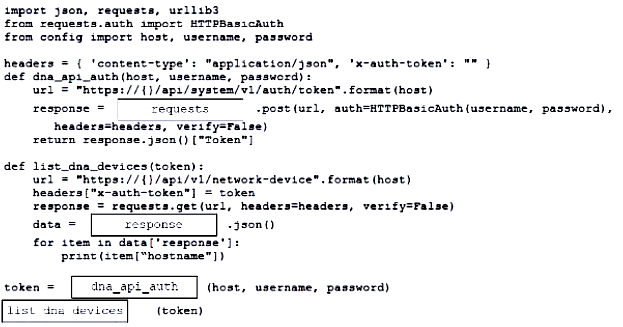
Question #: 319
Topic #: 1
DRAG DROP
–
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a request that generates a security token and gets a list of network devices. Not all options are used.
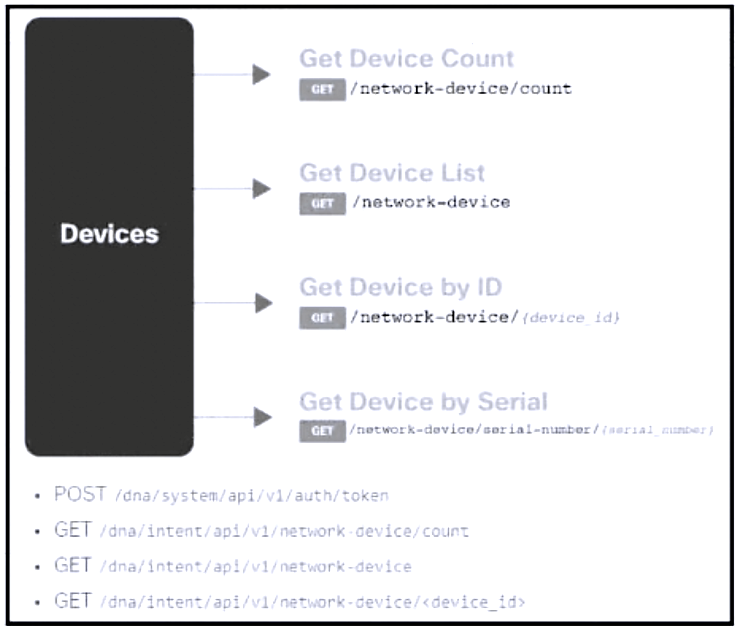
Suggestion Answer:
Question #: 320
Topic #: 1
Refer to the exhibit. A network engineer executes the bash script shown. Which two things are achieved by running the script? (Choose two.)
A. A directory called PRODUCTION is created.
B. The engineer changes to the parent directory.
C. A YAML file is created.
D. A YAML file is removed.
E. A directory called state.yml is created.
Selected Answer: AC
Question #: 321
Topic #: 1
DRAG DROP
–
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. The Python script retrieves a list of tasks from a to-do list for effective project management purposes. Not all options are used.
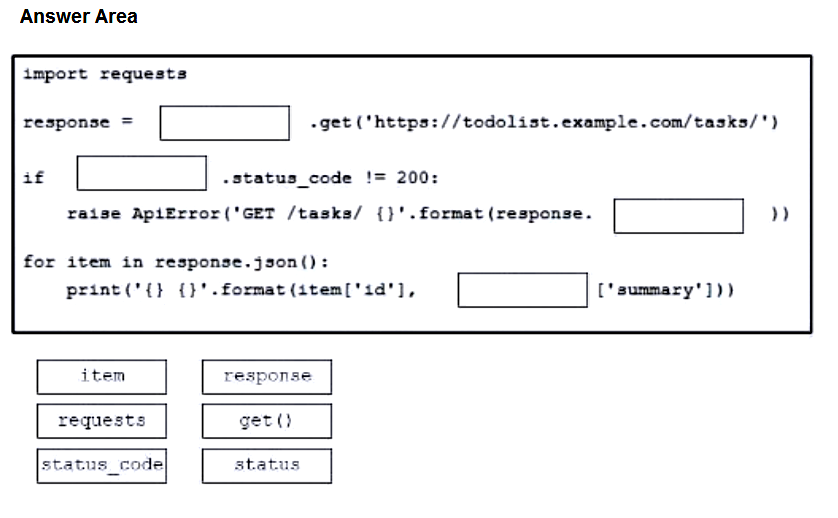
Suggestion Answer:
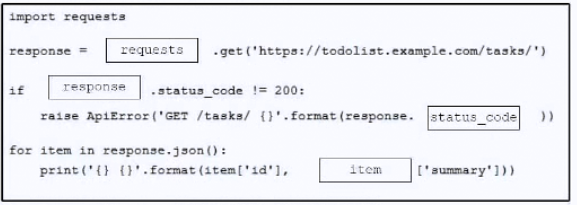
Question #: 322
Topic #: 1
Refer to the exhibit. Which code snippet represents the sequence.
A.
B.
C.
D.
Selected Answer: A
Question #: 323
Topic #: 1
A developer attempts to refactor and improve the application code. It is noticed that the code contains several pieces of key information that could be a security threat if this code is accessible by those who are not authorized to this data. Which approach addresses the security concerns noticed by the developer?
A. Host the application code on a machine located in a secure data center.
B. Utilize environment variables for username and password details.
C. Rely on the security teams’ goodwill to not give access to those who do not need it.
D. Move the hardware that the application is deployed on to a secure location.
Selected Answer: B
Question #: 324
Topic #: 1
DRAG DROP
–
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
Suggestion Answer:
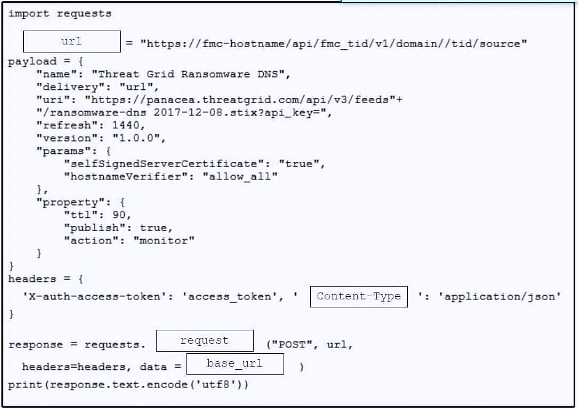
Question #: 325
Topic #: 1
Which tool provides a testing environment to run tests on network devices and perform network automation scenarios?
A. Visual Studio Code
B. Cisco VIRL
C. pyATS
D. Cisco Packet Tracer
Selected Answer: D
Question #: 326
Topic #: 1
A developer writes an application that refines data in temporary secure file storage hosted on the public cloud. Data will be deleted after processing and does not contain any private information. What is the advantage that a public cloud deployment provides to the developer?
A. high security with encryption
B. ease in infrastructure management
C. flexible development
D. bespoke services
Selected Answer: B
Question #: 327
Topic #: 1
DRAG DROP
–
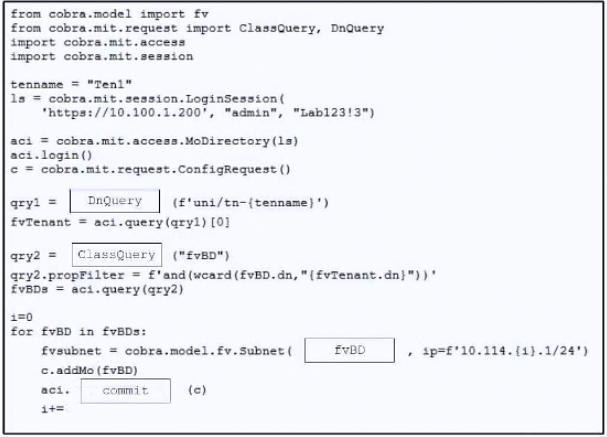
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to add a subnet to each bridge domain in the Ten1 tenant. Not all options are used.
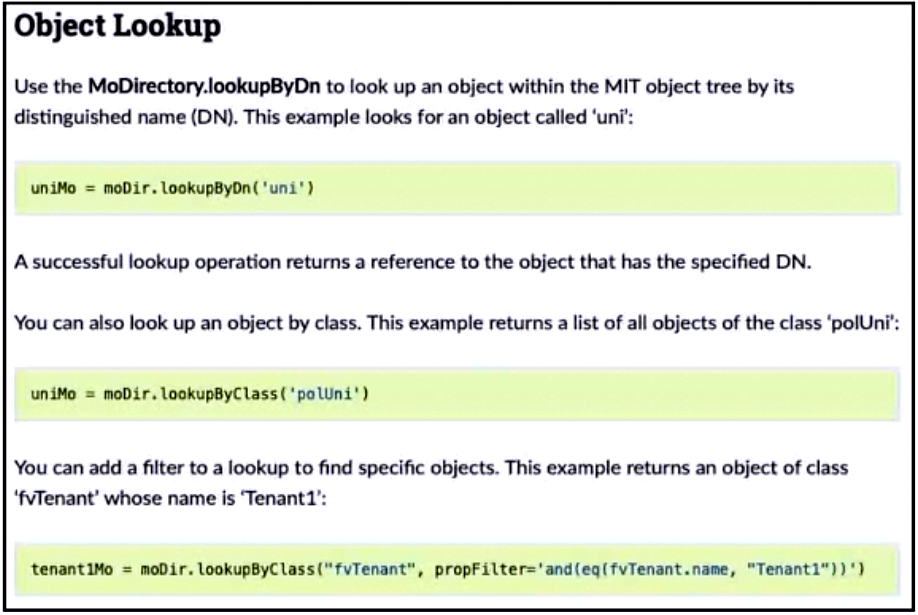
Suggestion Answer:
Question #: 328
Topic #: 1
Refer to the exhibit. A network engineer must copy the “config.txt” file from directory TEST to directory PROD. The copied file must also be renamed into “current.txt”. Which command must be used to accomplish these tasks?
A. cp ./PROD/current.txt ./TEST/config.txt
B. cp ./TESTi/current.txt ./PROD/config.txt
C. cp ./PROD/config.txt ./TEST/current.txt
D. cp ./TEST/config.txt ./PROD/current.txt
Selected Answer: D
Question #: 329
Topic #: 1
What is a benefit of using model-driven programmability for infrastructure automation?
A. connected user tracking
B. infrastructure resource optimization
C. multiple device control protocols
D. device performance monitoring
Selected Answer: B
Question #: 330
Topic #: 1
What is the function of an Ethernet switch in a networking environment?
A. to switch a frame from one port to another port based on IP address
B. to switch a frame from one port to another port based on MAC address
C. to provide IP addressing to connected hosts
D. to block unwanted traffic
Selected Answer: B
Question #: 331
Topic #: 1
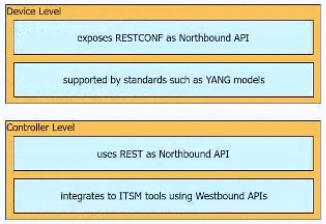
DRAG DROP
–
Drag and drop characteristics from the left onto the infrastructure management methodologies on the right.
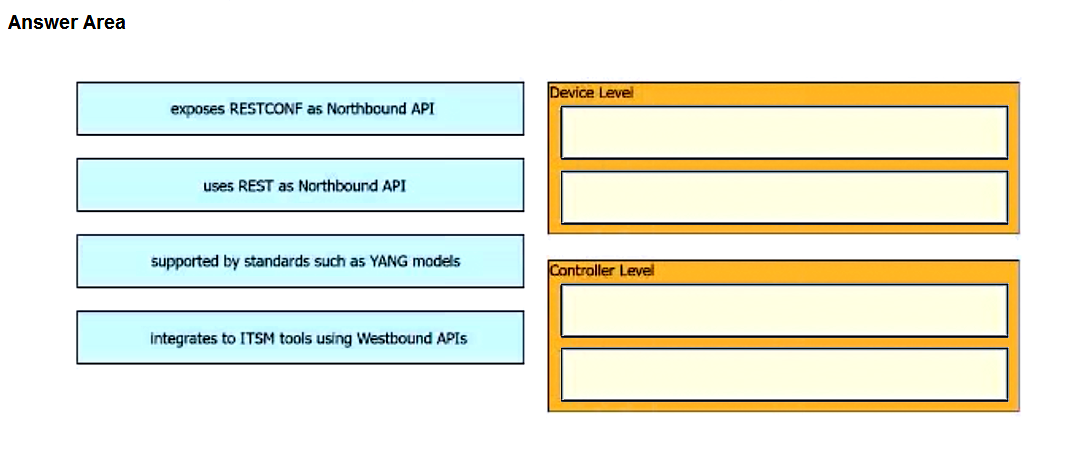
Suggestion Answer:
Question #: 332
Topic #: 1
Refer to the exhibit. An engineer runs a network that consists of Cisco Nexus devices. The network is distributed between data centers in different locations. The switches are configured using standalone connections and a single point of failure. Which process is being automated by the Ansible playbook?
A. enabling HSRP on the nxos_rtr inventory host
B. enabling HSRP on the rtr-1a inventory host
C. executing HSRP configuration from the Ansible controller node
D. executing HSRP configuration from the srv-1a inventory host
Selected Answer: D
Question #: 333
Topic #: 1
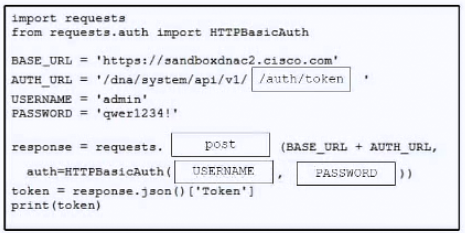
Refer to the exhibit. A developer must use a token to collect data from Cisco DNA Center API and prepares a Python script to send requests. Which line of code needs to be placed on the snippet where the code is missing to obtain a token from the Cisco DNA Center API?
A. token=BasicAuth(‘user’,‘password’))
B. auth=BasicAuth(‘user’,‘password’))
C. auth=HTTPBasicAuth(user,password))
D. token=HTTPBasicAuth(user,password))
Selected Answer: C
Question #: 334
Topic #: 1
To which stage of development do Infrastructure as Code principles relate?
A. manual configuration
B. service provisioning
C. physical deployment
D. requirement collection
Selected Answer: B
Question #: 335
Topic #: 1
Refer to the exhibit. An engineer must authorize a REST API call. The API password is “Cisco123!”. Which Bash command must be placed in the code to authorize the call?
A. mkdir API_PASSWORD=Cisco123!
B. set API_PASSWORD=Cisco123!
C. cp API_PASSWORD=Cisco123!
D. export API_PASSWORD=Cisco123!
Selected Answer: D
Question #: 336
Topic #: 1
DRAG DROP
–
Refer to the exhibit. Drag and drop the Dockerfile contents from the left onto the functions on the right that create a container image to run traceroute to track network path to specific targets. Not all options are used.
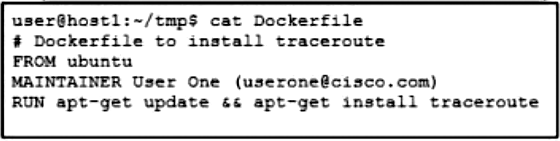
Suggestion Answer:
Question #: 337
Topic #: 1
Which function does a router provide to a network?
A. broadcast domain segmentation
B. unique host on a Layer 3 network
C. unique hardware address for every node on a LAN
D. broadcast domain extension
Selected Answer: A
Question #: 338
Topic #: 1
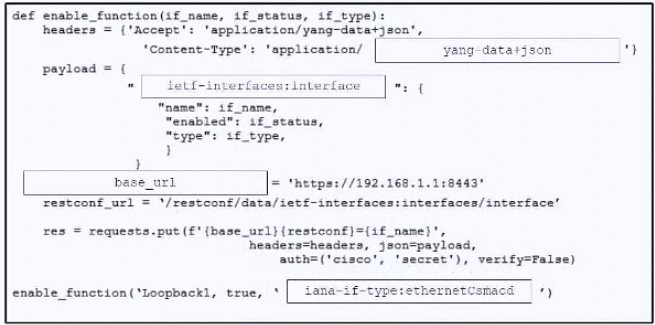
DRAG DROP
–
Drag and drop the code from the bottom onto the box where the code is missing to enable ports on a switch by using RESTCONF. Not all options are used.
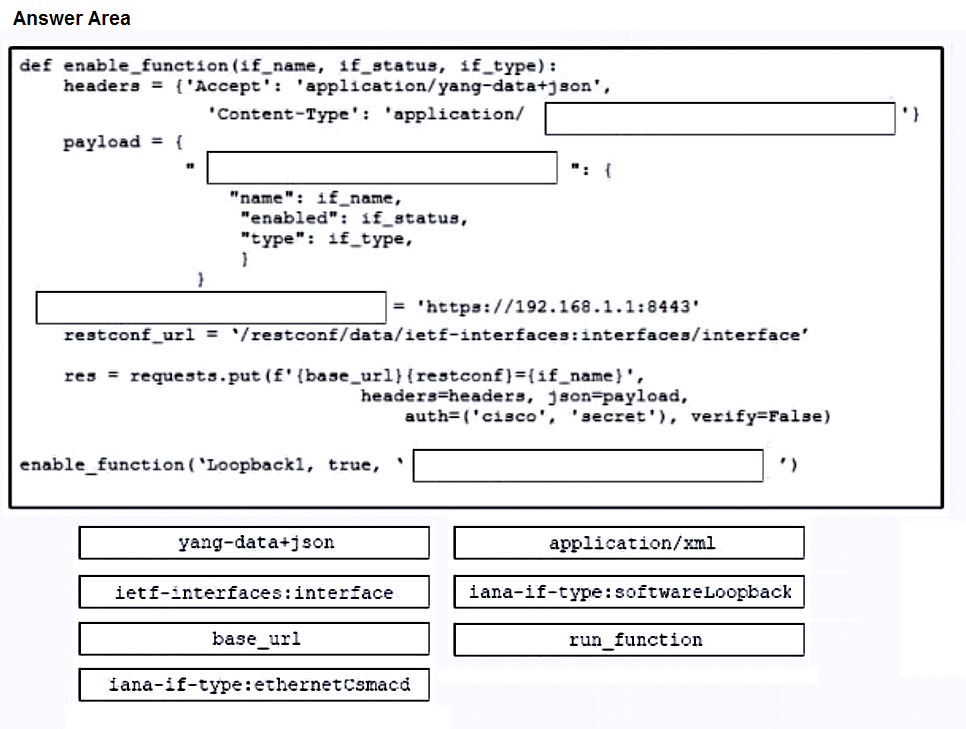
Suggestion Answer:
Question #: 339
Topic #: 1
Which IP service is used to monitor the performance of network devices?
A. SNMP
B. DHCP
C. DNS
D. NTP
Selected Answer: A
Question #: 340
Topic #: 1
Which IP service synchronizes the time across devices?
A. DNS
B. NTP
C. SNMP
D. NAT
Selected Answer: B
Question #: 341
Topic #: 1
An engineer must configure Cisco Nexus devices and wants to automate this workflow. The engineer will use an Ansible playbook to configure devices through Cisco NX REST API. Before the code is run, which resource must be used to verify that the REST API requests work as expected?
A. Cisco Open NX-OS
B. Cisco NX-OS SDK
C. Cisco Learning Labs
D. Cisco Code Exchange for Nexus
Selected Answer: A
Question #: 342
Topic #: 1
What is a function of the default gateway in a network?
A. to drop traffic that is destined to the default gateway
B. to forward traffic to different subnets
C. to forward traffic to the same subnet
D. to drop traffic that is not destined to the default gateway
Selected Answer: C
Question #: 343
Topic #: 1
What is a firehose webhook?
A. It collects data from third-party cloud APIs for custom applications.
B. It enables an application to receive real-time data from Cisco Webex.
C. It enables data to flow from the Cisco Webex API to a user’s application.
D. It sends a notification of any event for commonly used resources.
Selected Answer: D
Question #: 344
Topic #: 1
Which command reverses the last commit without changing the index file or the working tree position?
A. git revert HEAD
B. git reset –hard HEAD~3
C. git reset –soft HEAD^
D. git revert
Selected Answer: C
Question #: 345
Topic #: 1
DRAG DROP
–
Drag and drop the code from the bottom onto the box where the code is missing to complete the error path scenario. Not all options are used.
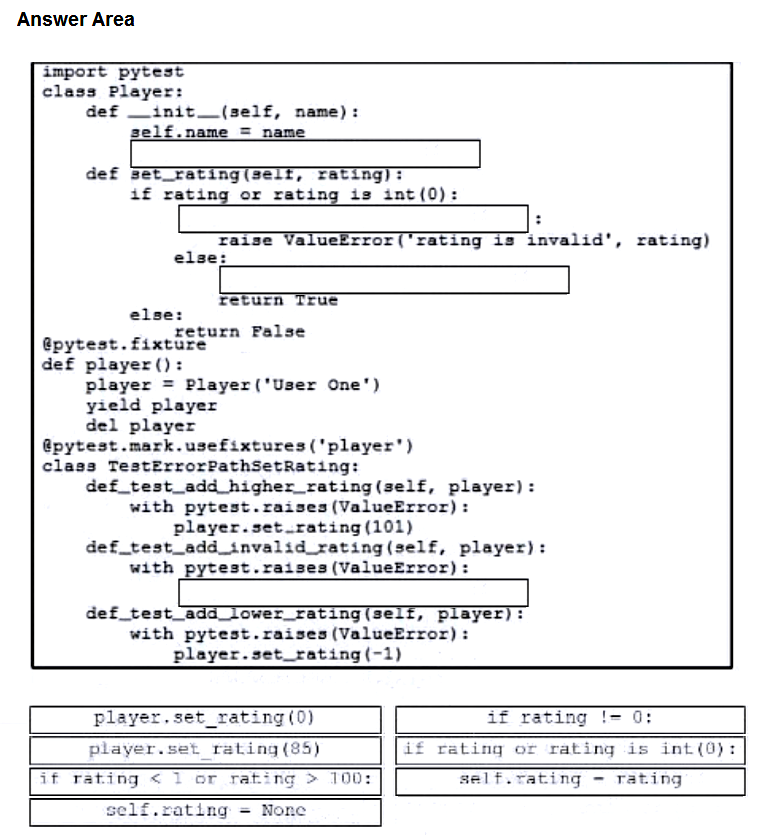
Suggestion Answer:
Question #: 346
Topic #: 1
A file in a local Git repository has been updated and issued the git add . command. The git diff command has been run to compare the changes to the previous commit, but nothing shows. Which action identifies the problem?
A. Run the git add . command again in the correct subdirectory to ensure changes added to the staging area.
B. Run the git commit command before the differences are compared to receive the end state of the code.
C. Run the git status command to see the differences between current and previous code review stages.
D. Run the git diff –staged command to compare the code added to the staging area.
Selected Answer: D
Question #: 347
Topic #: 1
DRAG DROP
–
Drag and drop the characteristics from the left onto the corresponding categories on the right to compare RESTful and RPC APIs.
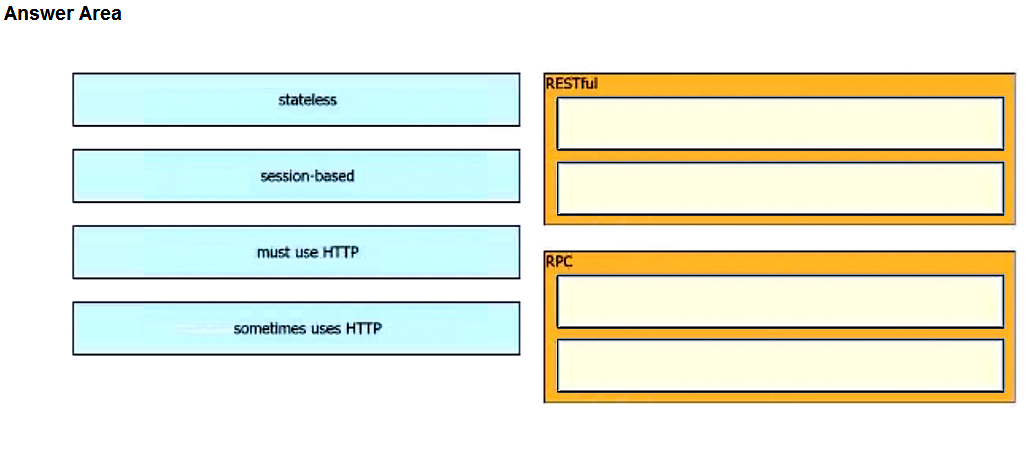
Suggestion Answer:

Question #: 348
Topic #: 1
Which protocol runs over TCP port 830?
A. NETCONF
B. Telnet
C. RESTCONF
D. HTTP
Selected Answer: A
Question #: 349
Topic #: 1
DRAG DROP
–
Drag and drop the code from the bottom onto the box where the code is missing to authenticate with the Cisco DNA Center REST API by using basic authentication. Then generate a token for later use. Not all options are used.
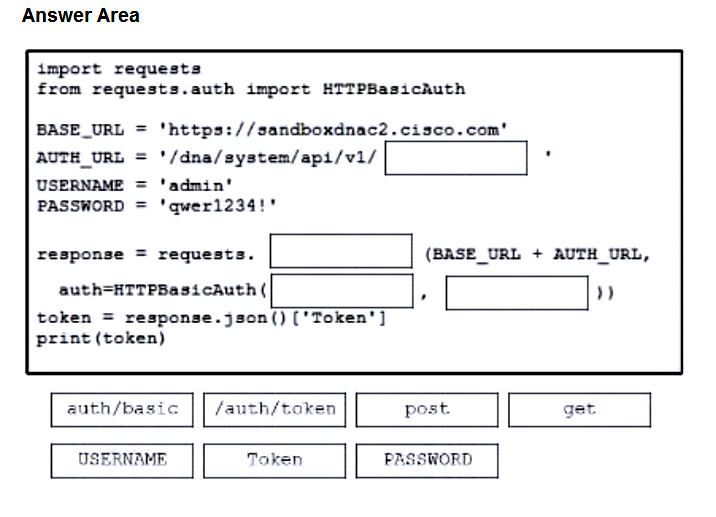
Suggestion Answer:
Question #: 350
Topic #: 1
Which solution reduces costs from MPLS, improves application performance, and simplifies operations?
A. Cisco NSO
B. Cisco SD-WAN
C. Cisco ACI
D. Cisco DNA Center
Selected Answer: B
Question #: 351
Topic #: 1
A developer has experienced security issues with a previously developed application. The API offered by that application is open and without any constraints. During a recent attack, the application was overloaded with API requests. To address this issue, an API constraint is implemented to protect the application from future attacks or any sudden throttling. Which API constraint must the application developer implement in this situation?
A. pagination
B. rate limiting
C. filtering
D. payload limiting
Selected Answer: B
Question #: 352
Topic #: 1
DRAG DROP
–
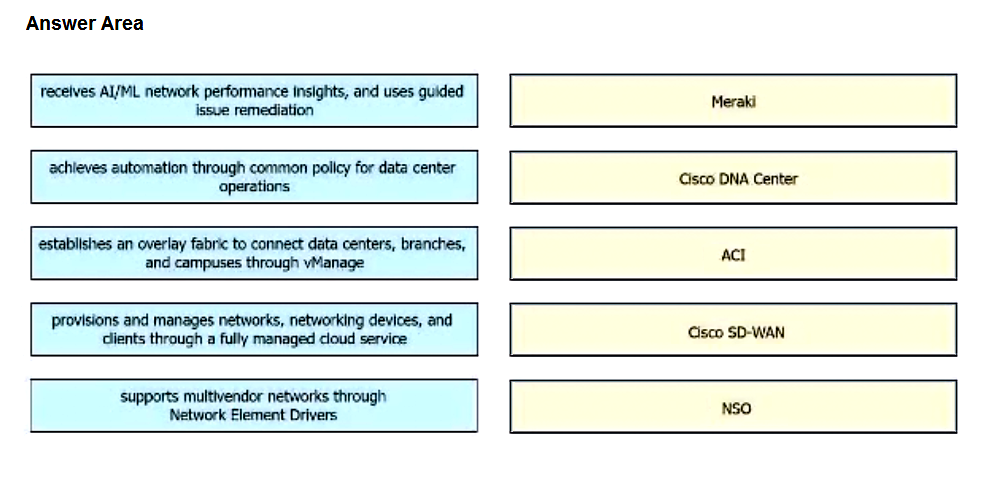
Drag and drop the capabilities from the left onto the Cisco Network Management Platforms that support the capabilities on the right.
Suggestion Answer:
Question #: 353
Topic #: 1
A developer must test the performance and reliability of an application. After functional and load tests are run, the application crashes due to traffic spikes from users. Which type of API constraint must be implemented to maintain reliability?
A. rate limiting
B. pagination
C. payload limits
D. filtering
Selected Answer: A
Question #: 354
Topic #: 1
DRAG DROP
–
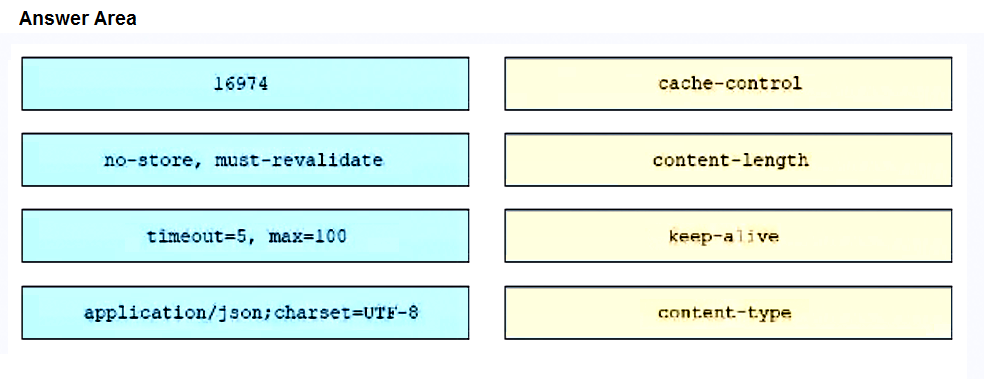
An engineer must make changes on a network device through the management platform API. The engineer prepares a script to send the request and analyze the response, check headers, and read the body according to information inside response headers. Drag and drop the HTTP header values from the left onto the elements of an HTTP response on the right.
Suggestion Answer:
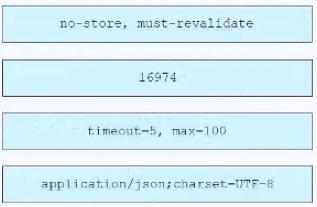
Question #: 355
Topic #: 1
A developer is working on a new feature in a branch named ‘newfeat123456789’ and the current working primary branch is named ‘prim987654321’. The developer requires a merge commit during a fast forward merge for record-keeping purposes. Which Git command must be used?
A. git merge –no-ff newfeat123456789
B. git commit –no-ff newfeat123456789
C. git add –commit-ff newfeat123456789
D. git reset –commit-ff newfeat123456789
Selected Answer: A
Question #: 356
Topic #: 1
A customer’s cloud services must:
• Migrate services to another data center on demand.
• Save the operational state of the machine on demand.
• Support Windows and Linux GUIs.
• Maximize hardware utilization.
Which type of deployment meets these requirements?
A. bare metal
B. container
C. virtual machine
D. Kubernetes
Selected Answer: C
Question #: 357
Topic #: 1
How does edge computing analyze sensitive data in the context of privacy control?
A. locally instead of sending the data to the cloud for analysis
B. locally or on the cloud depending on the configuration
C. all at once by sending the data to the cloud
D. locally on each node, and then sends the data to the cloud
Selected Answer: A
Question #: 358
Topic #: 1
Which Python function is used to parse a string that contains JSON data into a Python dictionary?
A. json.dumps()
B. json.to_json()
C. json.parse()
D. json.loads()
Selected Answer: D
Question #: 359
Topic #: 1
Refer to the exhibit. An engineer prepares a script to automate workflow by using Cisco DNA Center APIs to display:
• total count of devices
• list of the network devices
• information of one device with a hostname filter
What is displayed in the final step after the Python script is executed?
A. information about a device of type C9500-40x.
B. filtered results by the hostname and the platformld C9500-40X
C. information about the test devices
D. list of devices with platformId C9500-40x
Selected Answer: A
Question #: 360
Topic #: 1
A team of developers is responsible for a network orchestration application in the company. The responsibilities also include:
• developing and improving the application in a continuous manner
• deployment of the application and management of CI/CD frameworks
• monitoring the usage and problems and managing the performance improvements
Which principle best describes this DevOps practice?
A. responsible for IT operations
B. automation of processes
C. end-to-end responsibility
D. quality assurance checks
Selected Answer: C

