200-301: Cisco Certified Network Associate (CCNA) Part 10
Question #: 541
Topic #: 1
When the active router in an HSRP group fails, which router assumes the role and forwards packets?
A. forwarding
B. listening
C. standby
D. backup
Selected Answer: C
Question #: 542
Topic #: 1
When the active router in an HSRP group fails, which router assumes the role and forwards packets?
A. forwarding
B. listening
C. standby
D. backup
Selected Answer: C
Question #: 543
Topic #: 1
What protocol allows an engineer to back up 20 network router configurations globally while using the copy function?
A. TCP
B. SMTP
C. FTP
D. SNMP
Selected Answer: D
Question #: 544
Topic #: 1
Which type of address is the public IP address of a NAT device?
A. outside global
B. outside local
C. inside global
D. inside local
E. outside public
F. inside public
Selected Answer: C
Question #: 545
Topic #: 1
Which two pieces of information can you determine from the output of the show ntp status command? (Choose two.)
A. whether the NTP peer is statically configured
B. the IP address of the peer to which the clock is synchronized
C. the configured NTP servers
D. whether the clock is synchronized
E. the NTP version number of the peer
Selected Answer: BD
Question #: 546
Topic #: 1
Which keyword in a NAT configuration enables the use of one outside IP address for multiple inside hosts?
A. source
B. static
C. pool
D. overload
Selected Answer: D
Question #: 547
Topic #: 1
Which feature or protocol determines whether the QOS on the network is sufficient to support IP services?
A. LLDP
B. CDP
C. IP SLA
D. EEM
Selected Answer: C
Question #: 548
Topic #: 1
In QoS, which prioritization method is appropriate for interactive voice and video?
A. traffic policing
B. round-robin scheduling
C. low-latency queuing
D. expedited forwarding
Selected Answer: D
Question #: 549
Topic #: 1
DRAG DROP –
Drag and drop the SNMP components from the left onto the descriptions on the right.
Select and Place:
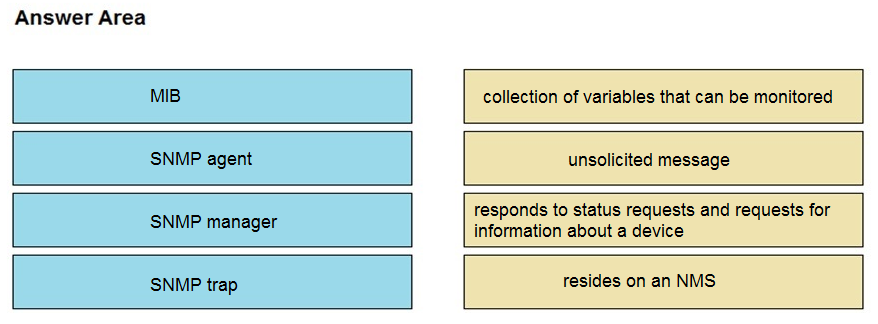
Suggestion Answer:
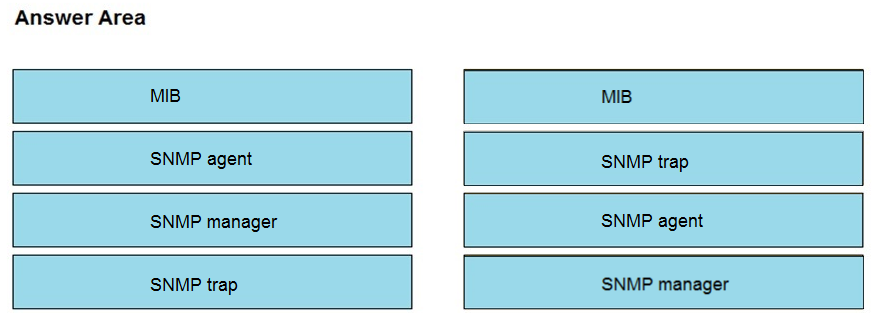
Question #: 550
Topic #: 1
What is the purpose of traffic shaping?
A. to be a marking mechanism that identifies different flows
B. to provide fair queuing for buffered flows
C. to mitigate delays over slow links
D. to limit the bandwidth that a flow can use
Selected Answer: D
Question #: 551
Topic #: 1
What is a function of TFTP in network operations?
A. transfers IOS images from a server to a router for firmware upgrades
B. transfers a backup configuration file from a server to a switch using a username and password
C. transfers configuration files from a server to a router on a congested link
D. transfers files between file systems on a router
Selected Answer: A
Question #: 552
Topic #: 1
What is a DHCP client?
A. a workstation that requests a domain name associated with its IP address
B. a host that is configured to request an IP address automatically
C. a server that dynamically assigns IP addresses to hosts.
D. a router that statically assigns IP addresses to hosts.
Selected Answer: B
Question #: 553
Topic #: 1
Where does the configuration reside when a helper address is configured lo support DHCP?
A. on the router closest to the server
B. on the router closest to the client
C. on every router along the path
D. on the switch trunk interface
Selected Answer: B
Question #: 554
Topic #: 1
What facilitates a Telnet connection between devices by entering the device name?
A. SNMP
B. DNS lookup
C. syslog
D. NTP
Selected Answer: B
Question #: 555
Topic #: 1
When deploying syslog, which severity level logs informational messages?
A. 0
B. 2
C. 4
D. 6
Selected Answer: D
Question #: 556
Topic #: 1
DRAG DROP –
Refer to the exhibit. An engineer is configuring the router to provide static NAT for the webserver. Drag and drop the configuration commands from the left onto the letters that correspond to its position in the configuration on the fight.
Select and Place:
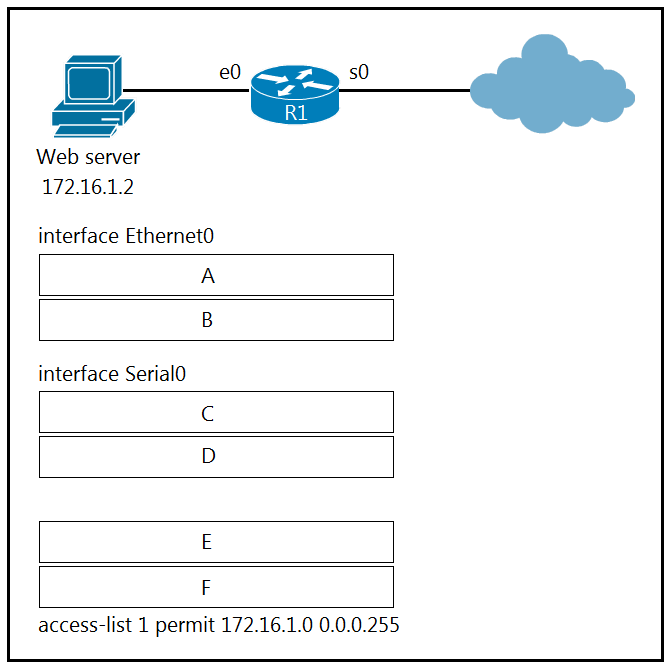
Suggestion Answer:
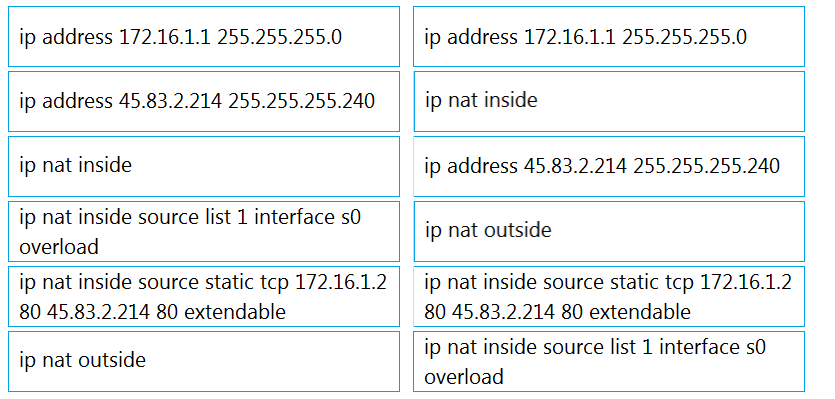
Question #: 557
Topic #: 1
Which two QoS tools provide congestion management? (Choose two.)
A. CBWFQ
B. FRTS
C. CAR
D. PBR
E. PQ
Selected Answer: AE
Question #: 558
Topic #: 1
Which QoS tool is used to optimize voice traffic on a network that is primarily intended for data traffic?
A. WRED
B. FIFO
C. WFQ
D. PQ
Selected Answer: D
Question #: 559
Topic #: 1
An engineer is installing a new wireless printer with a static IP address on the Wi-Fi network. Which feature must be enabled and configured to prevent connection issues with the printer?
A. client exclusion
B. DHCP address assignment
C. passive client
D. static IP tunneling
Selected Answer: C
Question #: 560
Topic #: 1
When a client and server are not on the same physical network, which device is used to forward requests and replies between client and server for DHCP?
A. DHCPOFFER
B. DHCP relay agent
C. DHCP server
D. DHCPDISCOVER
Selected Answer: B
Question #: 561
Topic #: 1
Refer to the exhibit. The ntp server 192.168.0.3 command has been configured on router 1 to make it an NTP client of router 2. Which command must be configured on router 2 so that it operates in server-only mode and relies only on its internal clock?
A. Router2(config)#ntp server 172.17.0.1
B. Router2(config)#ntp server 192.168.0.2
C. Router2(config)#ntp passive
D. Router2(config)#ntp master 4
Selected Answer: D
Question #: 562
Topic #: 1
Which protocol requires authentication to transfer a backup configuration file from a router to a remote server?
A. FTP
B. SMTP
C. TFTP
D. DTP
Selected Answer: A
Question #: 563
Topic #: 1
Which condition must be met before an NMS handles an SNMP trap from an agent?
A. The NMS must receive the same trap from two different SNMP agents to verify that it is reliable.
B. The NMS must receive a trap and an inform message from the SNMP agent within a configured interval.
C. The NMS software must be loaded with the MIB associated with the trap.
D. The NMS must be configured on the same router as the SNMP agent.
Selected Answer: C
Question #: 564
Topic #: 1
An engineer is configuring switch SW1 to act as an NTP server when all upstream NTP server connectivity fails. Which configuration must be used?
A. SW1# config t SW1(config)#ntp peer 192.168.1.1 SW1(config)#ntp access-group peer accesslist1
B. SW1# config t SW1(config)#ntp master SW1(config)#ntp server192.168.1.1
C. SW1# config t SW1(config)#ntp backup SW1(config)#ntp server192.168.1.1
D. SW1# config t SW1(config)#ntp server192.168.1.1 SW1(config)#ntp access-group peer accesslist1
Selected Answer: B
Question #: 565
Topic #: 1
A network administrator must enable DHCP services between two sites. What must be configured for the router to pass DHCPDISCOVER messages on to the server?
A. DHCP Binding
B. a DHCP Relay Agent
C. DHCP Snooping
D. a DHCP Pool
Selected Answer: B
Question #: 566
Topic #: 1
Which level of severity must be set to get informational syslogs?
A. alert
B. critical
C. notice
D. debug
Selected Answer: D
Question #: 567
Topic #: 1
On workstations running Microsoft Windows, which protocol provides the default gateway for the device?
A. STP
B. DHCP
C. SNMP
D. DNS
Selected Answer: B
Question #: 568
Topic #: 1
Which two statements about NTP operations are true? (Choose two.)
A. NTP uses UDP over IP.
B. Cisco routers can act as both NTP authoritative servers and NTP clients.
C. Cisco routers can act only as NTP servers.
D. Cisco routers can act only as NTP clients.
E. NTP uses TCP over IP.
Selected Answer: AB
Question #: 569
Topic #: 1
Refer to the exhibit. Which configuration must be applied to the router that configures PAT to translate all addresses in VLAN 200 while allowing devices on VLAN
100 to use their own IP addresses?
A. Router1(config)#access-list 99 permit 192.168.100.32 0.0.0.31 Router1(config)#ip nat inside source list 99 interface gi1/0/0 overload Router1(config)#interface gi2/0/1.200 Router1(config)#ip nat inside Router1(config)#interface gi1/0/0 Router1(config)#ip nat outside
B. Router1(config)#access-list 99 permit 192.168.100.0 0.0.0.255 Router1(config)#ip nat inside source list 99 interface gi1/0/0 overload Router1(config)#interface gi2/0/1.200 Router1(config)#ip nat inside Router1(config)#interface gi1/0/0 Router1(config)#ip nat outside
C. Router1(config)#access-list 99 permit 209.165.201.2 255.255.255.255 Router1(config)#ip nat inside source list 99 interface gi1/0/0 overload Router1(config)#interface gi2/0/1.200 Router1(config)#ip nat inside Router1(config)#interface gi1/0/0 Router1(config)#ip nat outside
D. Router1(config)#access- list 99 permit 209.165.201.2 0.0.0.0 Router1(config)#ip nat inside source list 99 interface gi1/0/0 overload Router1(config)#interface gi2/0/1.200 Router1(config)#ip nat inside Router1(config)#interface gi1/0/0 Router1(config)#ip nat outside
Selected Answer: A
Question #: 570
Topic #: 1
Refer to the exhibit. Which two commands must be added to update the configuration of router R1 so that it accepts only encrypted connections? (Choose two.)
A. transport input ssh
B. username CNAC secret R!41!3705926@
C. crypto key generate rsa 1024
D. line vty 0 4
E. ip ssh version 2
Selected Answer: AC
Question #: 571
Topic #: 1
Which command implies the use of SNMPv3?
A. snmp-server user
B. snmp-server host
C. snmp-server enable traps
D. snmp-server community
Selected Answer: A
Question #: 572
Topic #: 1
R1 as an NTP server must have:
✑ NTP authentication enabled
✑ NTP packets sourced from Interface loopback 0
✑ NTP stratum 2
✑ NTP packets only permitted to client IP 209.165.200.225
How should R1 be configured?
A. ntp authenticate ntp authentication-key 2 sha1 CISCO123 ntp source Loopback0 ntp access-group server-only 10 ntp master 2 ! access-list 10 permit udp host 209.165.200.225 any eq 123
B. ntp authenticate ntp authentication-key 2 md5 CISCO123 ntp interface Loopback0 ntp access-group server-only 10 ntp stratum 2 ! access-list 10 permit 209.165.200.225
C. ntp authenticate ntp authentication-key 2 md5 CISCO123 ntp source Loopback0 ntp access-group server-only 10 ntp master 2 ! access-list 10 permit 209.165.200.225
D. ntp authenticate ntp authentication-key 2 md5 CISCO123 ntp source Loopback0 ntp access-group server-only 10 ntp stratum 2 ! access-list 10 permit udp host 209.165.200.225 any eq 123
Selected Answer: C
Question #: 573
Topic #: 1
What is a capability of FTP in network management operations?
A. offers proprietary support at the session layer when transferring data
B. uses separate control and data connections to move files between server and client
C. encrypts data before sending between data resources
D. devices are directly connected and use UDP to pass file information
Selected Answer: B
Question #: 574
Topic #: 1
A network engineer is configuring a switch so that it is remotely reachable via SSH. The engineer has already configured the host name on the router. Which additional command must the engineer configure before entering the command to generate the RSA key?
A. password password
B. ip ssh authentication-retries 2
C. ip domain-name domain
D. crypto key generate rsa modulus 1024
Selected Answer: C
Question #: 575
Topic #: 1
Which QoS traffic handling technique retains excess packets in a queue and reschedules these packets for later transmission when the configured maximum bandwidth has been surpassed?
A. traffic policing
B. weighted random early detection
C. traffic prioritization
D. traffic shaping
Selected Answer: D
Question #: 576
Topic #: 1
Which command must be entered to configure a DHCP relay?
A. ip dhcp relay
B. ip dhcp pool
C. ip address dhcp
D. ip helper-address
Selected Answer: D
Question #: 577
Topic #: 1
Refer to the exhibit. The DHCP server and clients are connected to the same switch. What is the next step to complete the DHCP configuration to allow clients on
VLAN 1 to receive addresses from the DHCP server?
A. Configure the ip dhcp snooping trust command on the interface that is connected to the DHCP client.
B. Configure ip dhcp relay information option command on the interface that is connected to the DHCP server.
C. Configure ip dhcp snooping trust command on the interface that is connected to the DHCP server.
D. Configure the ip dhcp information option command on the interface that is connected to the DHCP client.
Selected Answer: C
Question #: 578
Topic #: 1
A network analyst is tasked with configuring the date and time on a router using EXEC mode. The date must be set to January 1, 2020 and the time must be set to
12:00 am. Which command should be used?
A. clock timezone
B. clock summer-time date
C. clock summer-time recurring
D. clock set
Selected Answer: D
Question #: 579
Topic #: 1
Refer to the exhibit. What is the metric of the route to the 192.168.10.33/28 subnet?
A. 84
B. 110
C. 192
D. 193
Selected Answer: D
Question #: 580
Topic #: 1
Which command creates a static NAT binding for a PC address of 10.1.1.1 to the public routable address 209.165.200.225 assigned to the PC?
A. R1(config)#ip nat inside source static 10.1.1.1 209.165.200.225
B. R1(config)#ip nat outside source static 209.165.200.225 10.1.1.1
C. R1(config)#ip nat inside source static 209.165.200.225 10.1.1.1
D. R1(config)#ip nat outside source static 10.1.1.1 209.165.200.225
Selected Answer: A
Question #: 581
Topic #: 1
What prevents a workstation from receiving a DHCP address?
A. STP
B. VTP
C. 802.1Q
D. DTP
Selected Answer: A
Question #: 582
Topic #: 1
What is a feature of TFTP?
A. offers anonymous user login ability
B. uses two separate connections for control and data traffic
C. relies on the well-known TCP port 20 to transmit data
D. provides secure data transfer
Selected Answer: A
Question #: 583
Topic #: 1
Which QoS forwarding per-hop behavior changes a specific value in a packet header to set the class of service for the packet?
A. shaping
B. classification
C. policing
D. marking
Selected Answer: D
Question #: 584
Topic #: 1
Refer to the exhibit. How should the configuration be updated to allow PC1 and PC2 access to the Internet?
A. Modify the configured number of the second access list
B. Change the ip nat inside source command to use interface GigabitEthernet0/0
C. Remove the overload keyword from the ip nat inside source command
D. Add either the ip nat {inside|outside} command under both interfaces
Selected Answer: B
Question #: 585
Topic #: 1
What is the purpose of the ip address dhcp command?
A. to configure an interface as a DHCP relay
B. to configure an interface as a DHCP client
C. to configure an interface as a DHCP helper
D. to configure an interface as a DHCP server
Selected Answer: B
Question #: 586
Topic #: 1
Refer to the exhibit. Which configuration enables DHCP addressing for hosts connected to interface FastEthernet0/1 on router R4?
A. interface FastEthernet0/1 ip helper-address 10.0.1.1 ! access-list 100 permit tcp host 10.0.1.1 eq 67 host 10.148.2.1
B. interface FastEthernet0/0 ip helper-address 10.0.1.1 ! access-list 100 permit udp host 10.0.1.1 eq bootps host 10.148.2.1
C. interface FastEthernet0/0 ip helper-address 10.0.1.1 ! access-list 100 permit host 10.0.1.1 host 10.148.2.1 eq bootps
D. interface FastEthernet0/1 ip helper-address 10.0.1.1 ! access-list 100 permit udp host 10.0.1.1 eq bootps host 10.148.2.1
Selected Answer: D
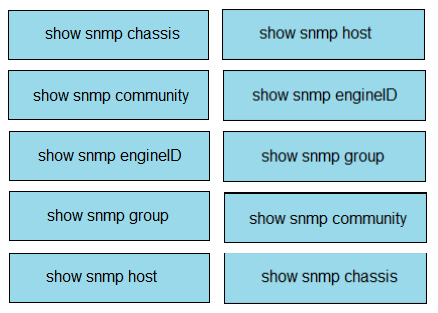
Question #: 587
Topic #: 1
DRAG DROP –
Drag and drop the SNMP manager and agent identifier commands from the left onto the functions on the right.
Select and Place:
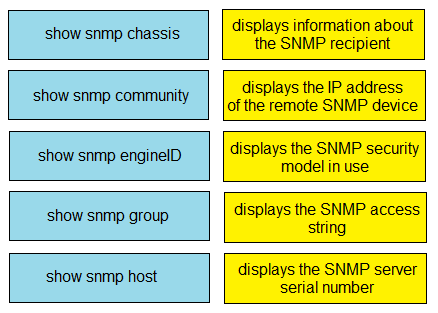
Suggestion Answer:
Question #: 588
Topic #: 1
An engineer is configuring SSH version 2 exclusively on the R1 router. What is the minimum configuration required to permit remote management using the cryptographic protocol?
A. hostname R1 service password-encryption crypto key generate rsa general-keys modulus 1024 username cisco privilege 15 password 0 cisco123 ip ssh version 2 line vty 0 15 transport input ssh login local
B. hostname R1 ip domain name cisco crypto key generate rsa general-keys modulus 1024 username cisco privilege 15 password 0 cisco123 ip ssh version 2 line vty 0 15 transport input ssh login local
C. hostname R1 crypto key generate rsa general-keys modulus 1024 username cisco privilege 15 password 0 cisco123 ip ssh version 2 line vty 0 15 transport input ssh login local
D. hostname R1 ip domain name cisco crypto key generate rsa general-keys modulus 1024 username cisco privilege 15 password 0 cisco123 ip ssh version 2 line vty 0 15 transport input all login local
Selected Answer: B
Question #: 589
Topic #: 1
Which per-hop traffic-control feature does an ISP implement to mitigate the potential negative effects of a customer exceeding its committed bandwidth?
A. policing
B. queuing
C. marking
D. shaping
Selected Answer: A
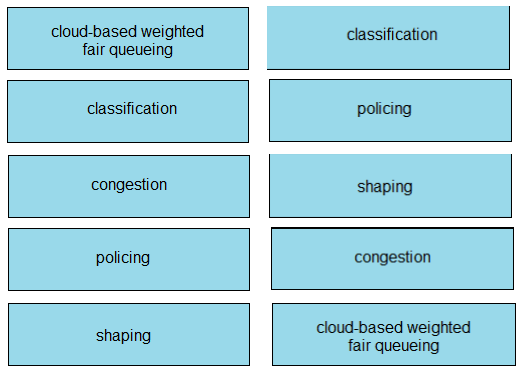
Question #: 590
Topic #: 1
DRAG DROP –
Drag and drop the QoS terms from the left onto the descriptions on the right.
Select and Place:
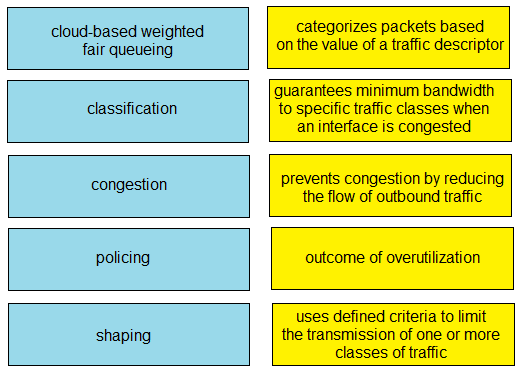
Suggestion Answer:
Question #: 591
Topic #: 1
Which remote access protocol provides unsecured remote CLI access?
A. console
B. Telnet
C. SSH
D. Bash
Selected Answer: B
Question #: 592
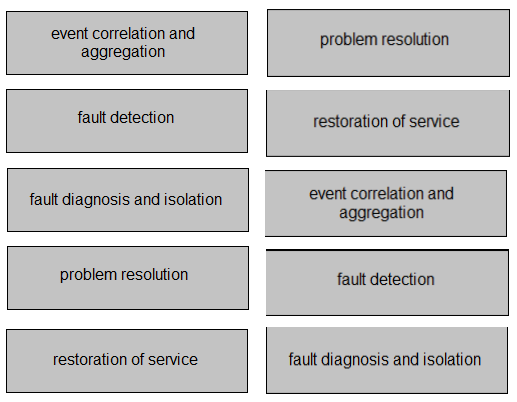
Topic #: 1
DRAG DROP –
Drag and drop the functions of SNMP fault-management from the left onto the definitions on the right.
Select and Place:
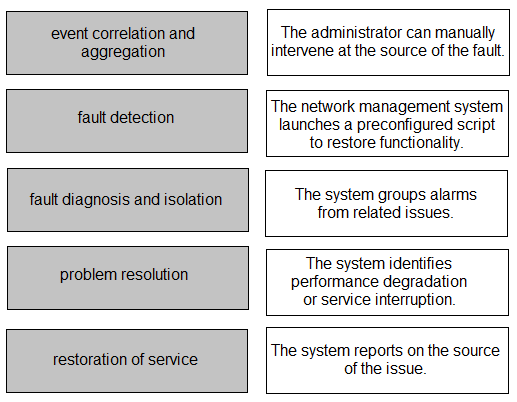
Suggestion Answer:
Question #: 593
Topic #: 1
Refer to the exhibit. Which router or router group are NTP clients?
A. R1
B. R2 and R3
C. R1, R3, and R4
D. R1, R2, and R3
Selected Answer: D
Question #: 594
Topic #: 1
Refer to the exhibit. What is the next step to complete the implementation for the partial NAT configuration shown?
A. Modify the access list for the internal network on e0/1.
B. Reconfigure the static NAT entries that overlap the NAT pool.
C. Apply the ACL to the pool configuration.
D. Configure the NAT outside interface.
Selected Answer: D
Question #: 595
Topic #: 1
What is a syslog facility?
A. host that is configured for the system to send log messages
B. password that authenticates a Network Management System to receive log messages
C. group of log messages associated with the configured severity level
D. set of values that represent the processes that can generate a log message
Selected Answer: D
Question #: 596
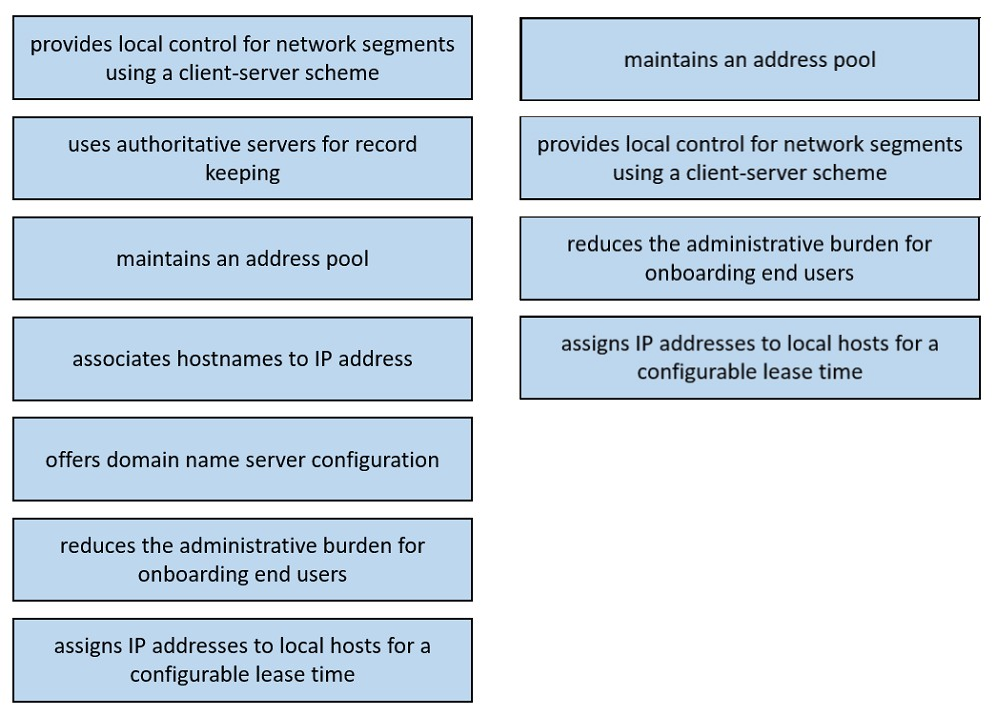
Topic #: 1
DRAG DROP –
Drag and drop the functions of DHCP from the left onto any of the positions on the right. Not all functions are used.
Select and Place:
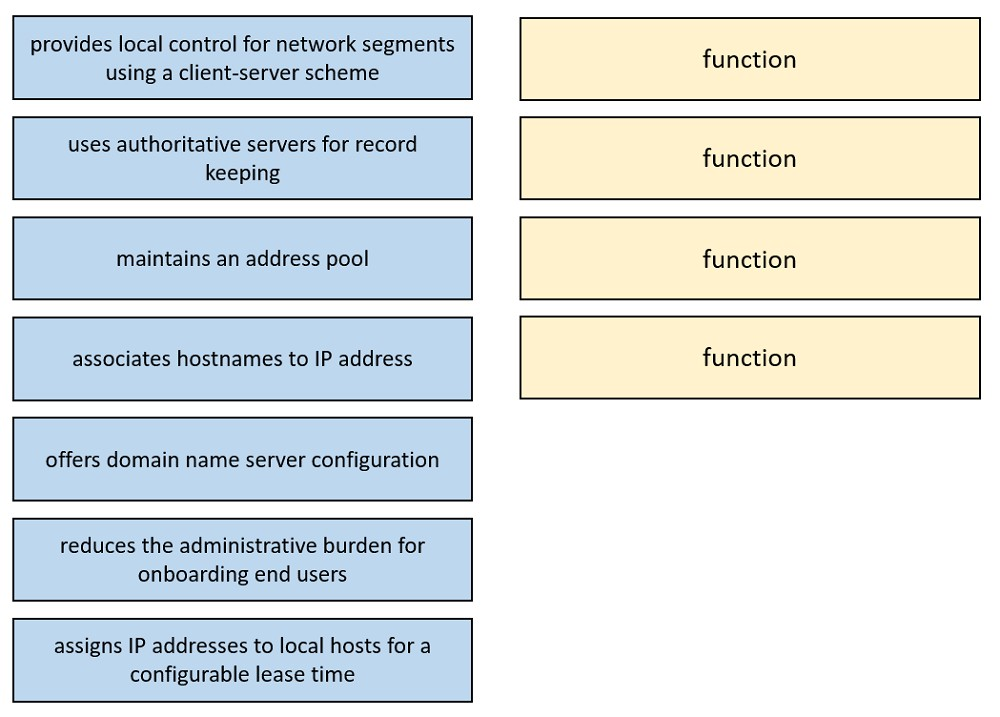
Suggestion Answer:
Question #: 597
Topic #: 1
Refer to the exhibit. A newly configured PC fails to connect to the internet by using TCP port 80 to www.cisco.com. Which setting must be modified for the connection to work?
A. Subnet Mask
B. DNS Servers
C. Default Gateway
D. DHCP Servers
Selected Answer: B
Question #: 598
Topic #: 1
Which QoS queuing method discards or marks packets that exceed the desired bit rate of traffic flow?
A. CBWFQ
B. policing
C. LLQ
D. shaping
Selected Answer: B
Question #: 599
Topic #: 1
Which QoS per-hop behavior changes the value of the ToS field in the IPv4 packet header?
A. Shaping
B. Policing
C. Classification
D. Marking
Selected Answer: D
Question #: 600
Topic #: 1
What is the function of FTP?
A. Always operated without user connection validation
B. Uses block number to identify and mitigate data-transfer errors
C. Relies on the well-known UDO port 69 for data transfer
D. Uses two separate connections for control and data traffic
Selected Answer: D

